In any blockchain platform, the consensus mechanism is a core component that shapes how a Layer 1 network functions, alongside other architectural elements of the chain.
So, what is a Blockchain Consensus Mechanism that makes Layer 1 networks different? Let's explore through this article.
What is Blockchain Consensus Mechanism?
A consensus algorithm in blockchain is a set of protocol rules in a distributed network that participating nodes must follow to reach agreement on the canonical state of the shared ledger. It defines how these participants propose, validate, and finalize new blocks of transactions.
Nodes are the individual computers or devices that run the blockchain software, keep a copy of the ledger, and take part in validating transactions.
It ensures that every transaction is validated consistently, securely, and immutably by the network, without the intervention of a central authority. As a result, a blockchain can maintain data integrity, resist attacks, remain fault tolerant even when some nodes fail or act maliciously, and ensure transparency in a decentralized system.
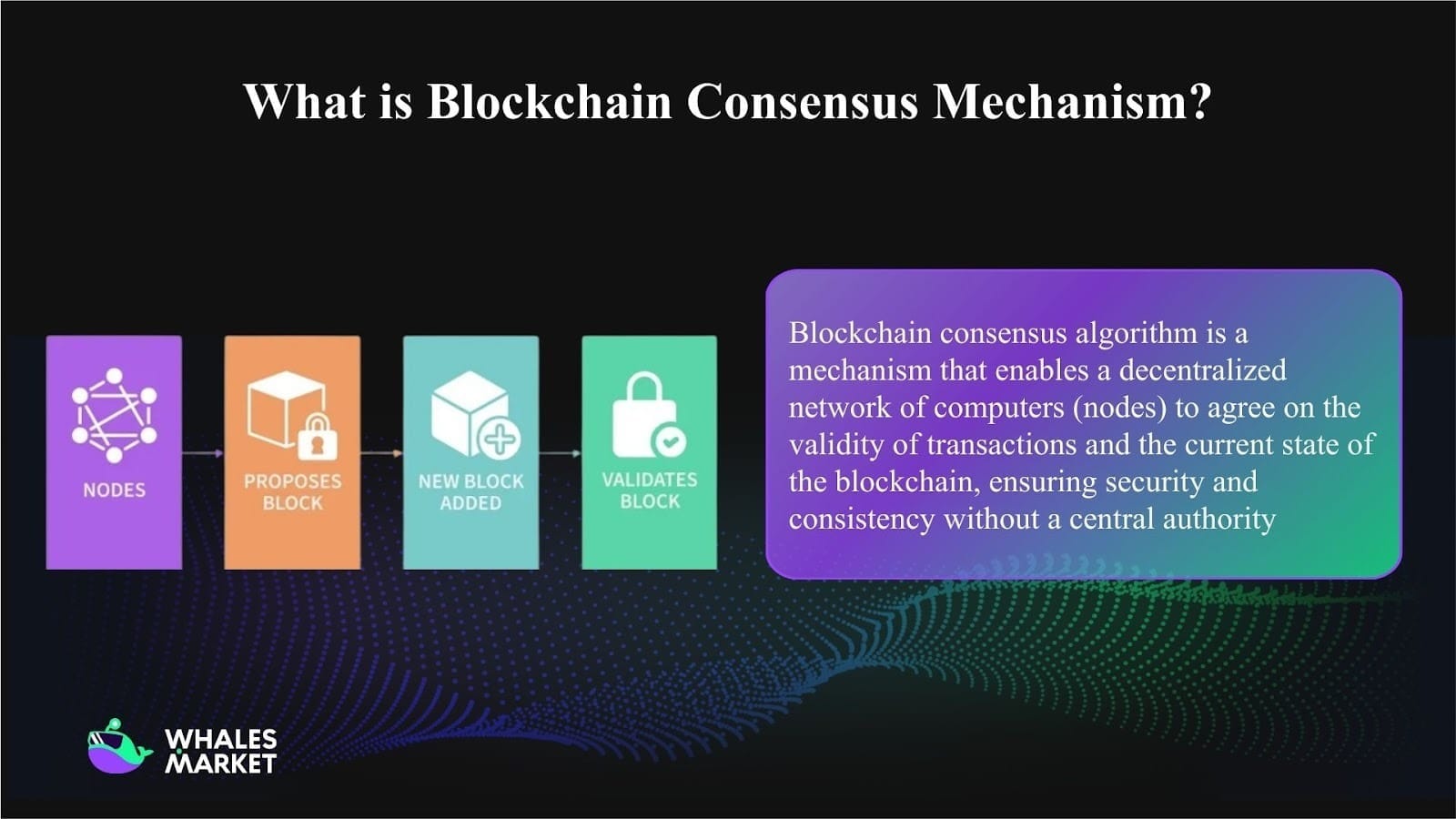
How does a consensus algorithm work?
To understand how blockchain consensus works, investors first need to grasp the concepts of nonce, hash and slashing:
- Hash: A hash is a string of characters generated from a piece of data using a hash function (such as SHA-256). If you change even one character in the original data, the resulting hash will be completely different, so hashes are used to check whether data has been altered. In a blockchain, each block has its own hash, which helps link the blocks together and protect the chain.
- Nonce: A nonce is a number that miners keep changing when they try to create a new block. The goal is to find a nonce such that the block’s hash meets the network’s requirement (usually that the hash starts with a certain number of zeros). Because there is no way to predict this in advance, miners must try millions or even billions of nonce values, which creates competition and helps secure Proof of Work networks.
- Slashing is a penalty mechanism in Proof of Stake mechanism, where part or all of a validator’s staked tokens are taken away (burned or confiscated) if they behave maliciously or break the protocol rules.
Essentially, a blockchain consists of many nodes that together form a network. For a transaction to be recorded on the blockchain, it must be validated by all participating nodes based on the network’s consensus mechanism.
First, it is important to understand that a blockchain is structured as multiple blocks linked together to form a chain. Each block contains information about the hash of the previous block. This hash is generated from predefined inputs of the block, including validated transaction data.

When a user submits a transaction, nodes use the blockchain’s consensus algorithm (such as PoS, PoW, PoA, etc.) to verify and record the transaction into a new block. Afterward, all nodes must download and update the newly validated block to ensure data consistency and integrity across the network.
The consensus mechanism also makes altering blockchain data nearly impossible:
- If the data inside a block is modified, the hash of that block also changes.
- This new hash will be compared with hashes of surrounding blocks to confirm whether the chain remains valid.
- If the hashes do not match, the modified data will be rejected and cannot be added to the blockchain.
For example, suppose a hacker attacks and alters information in block n:
The hash of block n will change.
- The system compares it with the previous block’s hash and detects inconsistency.
- To cover the change, the hacker would need to alter block n-1. The system would then detect inconsistency there as well.
- The hacker would have to continue modifying block n-2, and so on.
Therefore, to change a single transaction, the hacker must modify every subsequent block, which is practically infeasible under a functioning consensus mechanism.
Why does a blockchain need a consensus mechanism?
Ensures nodes perform their responsibilities
A blockchain operates in a decentralized manner through a global network of nodes, without any intermediary controlling or managing it.
So how can we ensure that these nodes correctly validate transactions, operate the blockchain properly, and do not commit fraud? This is where the consensus mechanism plays a crucial role.
Nodes are required to follow the consensus rules to perform their duties, and if they do not, they may be penalized through mechanisms such as slashing.
Enables blockchain to achieve Byzantine Fault Tolerance (BFT)
The “Byzantine Generals Problem” describes a scenario where multiple parties struggle to reach agreement on a coordinated action due to unreliable communication. For instance:
- If all (or the majority) agree to attack, they win.
- If only a minority attacks while the rest defend, they lose.
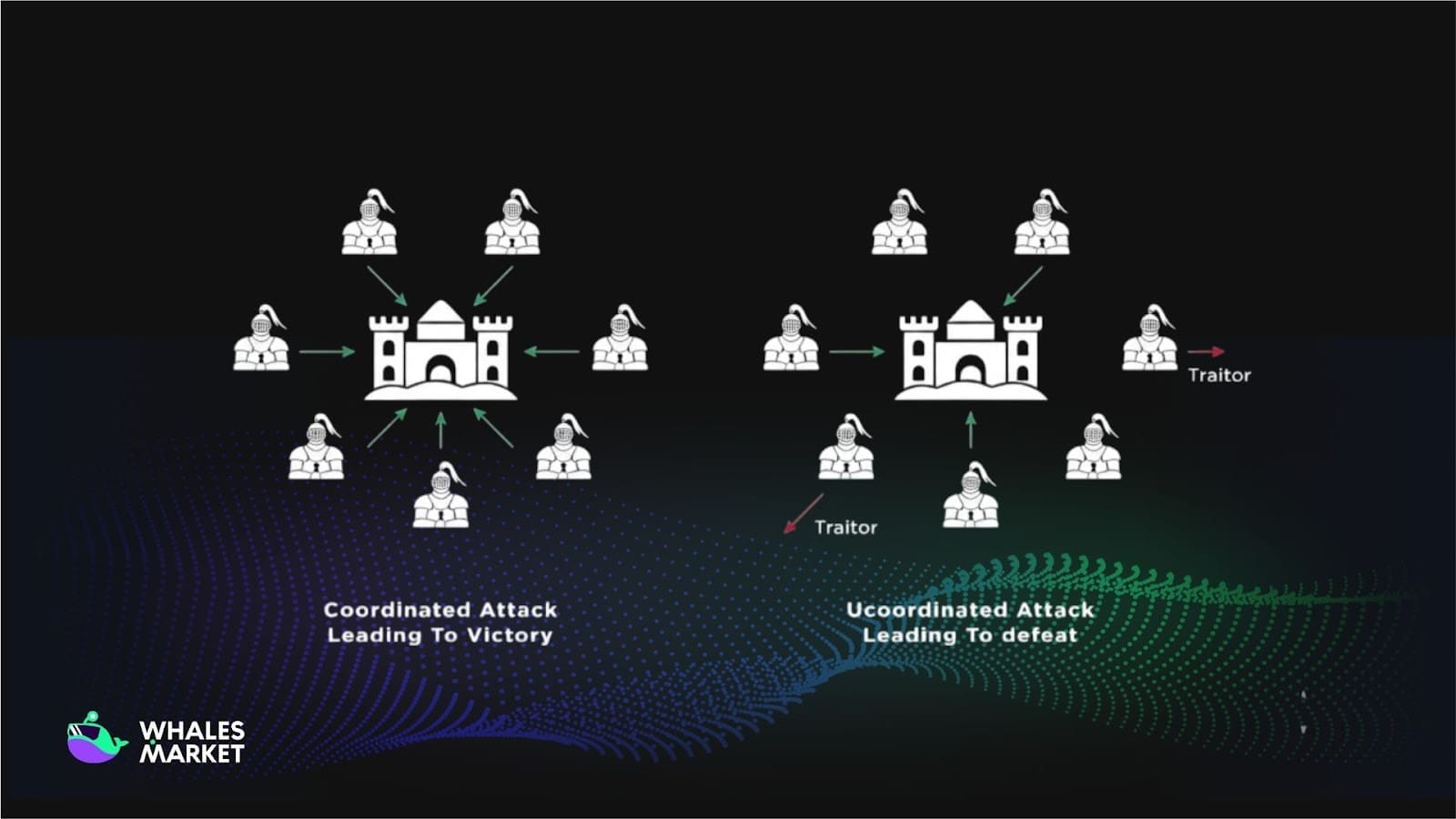
This becomes a challenging problem in computer science: in an environment where communication may fail, how can systems still operate reliably and reach agreement?
Thanks to consensus algorithms, blockchains can address this problem. As a result, a blockchain becomes a Byzantine Fault Tolerant (BFT) system, meaning the network can continue functioning even if some nodes fail, behave maliciously, or attempt to disrupt operations, as long as the majority comply with the consensus rules.
It is important to note that blockchains implement reward and penalty mechanisms to encourage nodes to follow the consensus protocol.
Types of Consensus Algorithms
There are many types of consensus algorithms developed to suit different needs of blockchains, from public to private, from high energy consumption to resource-efficient. The most common types include:
- Proof of Work (PoW)
- Proof of Stake (PoS)
- Delegated Proof of Stake (DPoS)
- Proof of Authority (PoA)
- Practical Byzantine Fault Tolerance (PBFT)
These types are chosen based on factors such as network scale, transaction speed, and required security level. Below is a detailed analysis of each type, based on how they operate in practice.
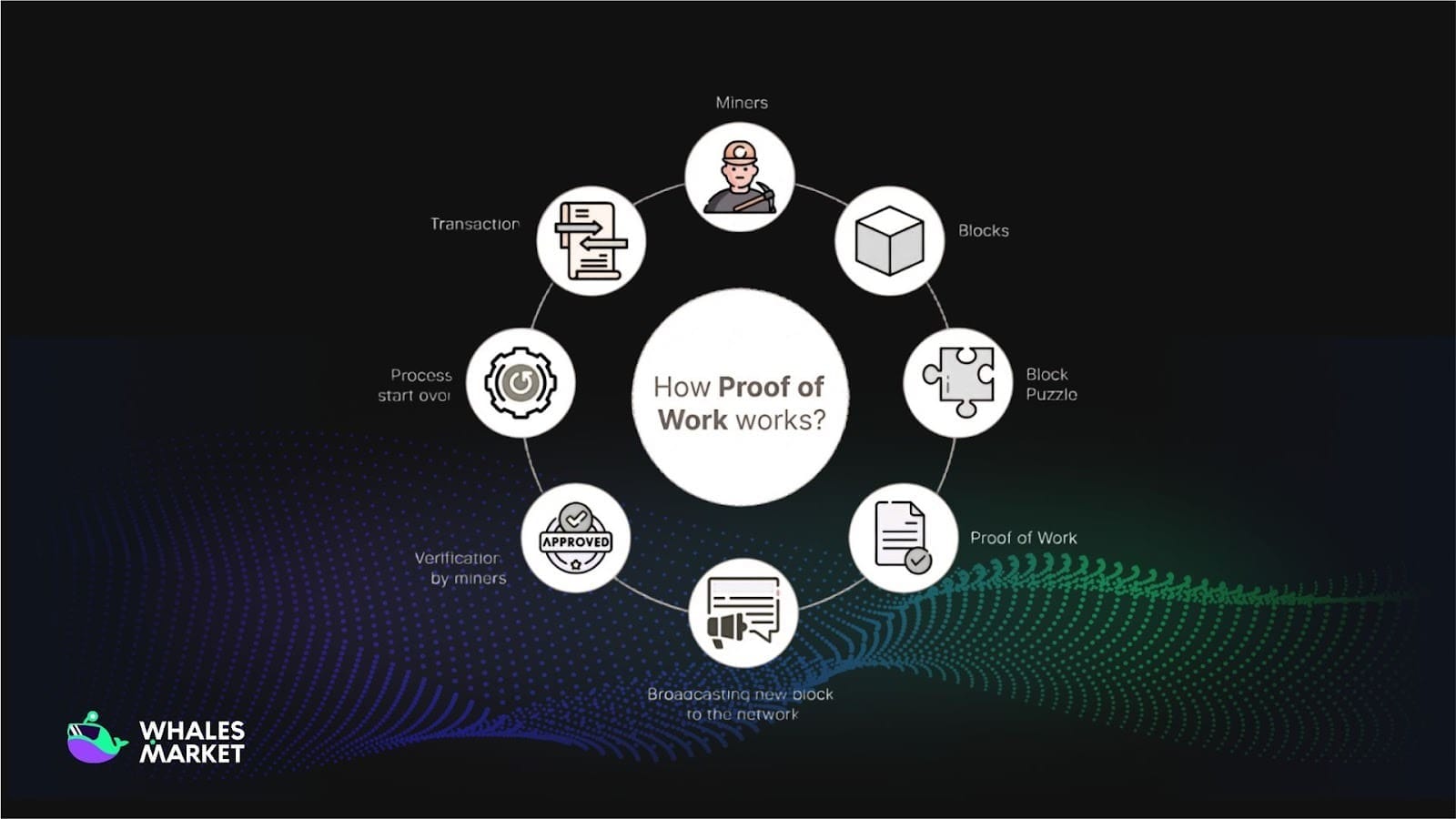
Proof of Work (PoW)
In Proof of Work (PoW), specialized nodes called miners compete to solve a complex mathematical puzzle (called cryptographic), often involving finding a nonce value such that the hash of the data block meets a specific condition (e.g., starting with a certain number of zeros).
The miner that solves it first earns the right to propose a new block. If this block is validated and accepted by the other nodes in the network, it is added to the chain and the miner receives a block reward
This process requires significant computational power, which is very expensive in terms of hardware and electricity. That high cost makes it economically impractical for any single party to gain enough hash power to control or attack the network (for example, through a 51% attack).
Advantages:
- High security due to the large resources required for an attack (needs control over more than 50% of the network's computational power).
- Proven over time, like in Bitcoin, helping the network withstand Byzantine faults well.
- Encourages decentralization by allowing anyone to participate in mining.
Disadvantages:
- Consumes a large amount of energy, leading to environmental issues and high costs.
- Slow transaction speeds (about 7-10 transactions per second on Bitcoin) due to long puzzle-solving times.
- Can lead to power concentration in large mining pools, reducing true decentralization.
Proof of Work is used by several major blockchains such as Bitcoin, Litecoin and Monero. These networks rely on computational power and hash algorithms to validate transactions and produce new blocks.
Proof of Stake (PoS)
Instead of computational competition, Proof of Stake (PoS) selects block validators based on the amount of tokens they stake in the network. Participants lock up assets as collateral, and the system randomly selects based on stake proportion to create new blocks. If they act fraudulently, their stake is forfeited. This encourages honest behavior without needing significant hardware power.
Advantages:
- Much more energy-efficient than PoW, environmentally friendly.
- Increases transaction speed and scalability (like Ethereum after switching to PoS).
- Reduces risk of power concentration by relying on assets rather than hardware.
Disadvantages:
- Can lead to a "rich get richer" situation, as those with more stake are more likely to be selected.
- Risk of attack if one party controls the majority of stake (though harder than PoW).
- Less battle-tested in reality compared to PoW, potentially with undiscovered vulnerabilities.
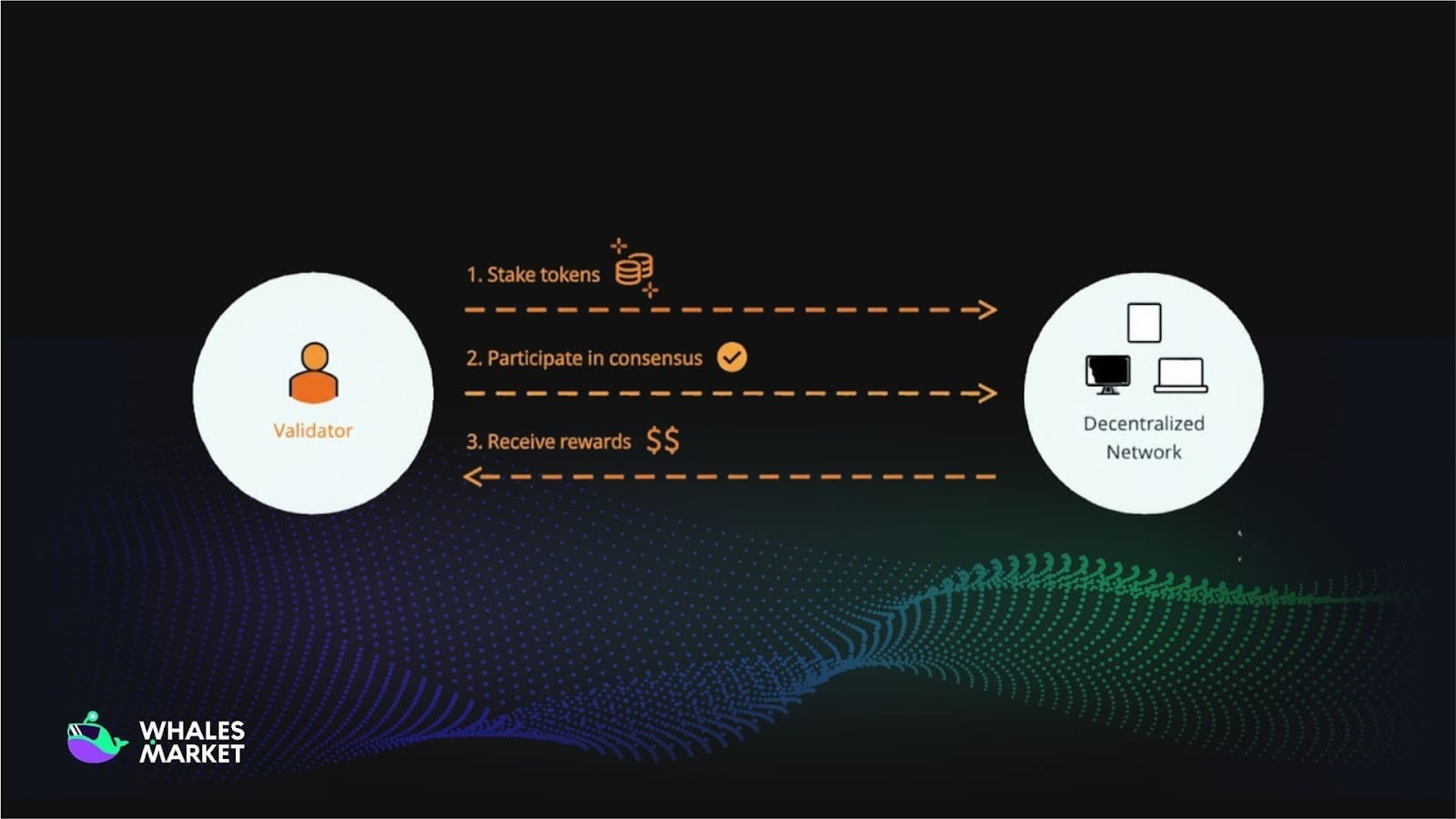
On September 15, 2022, Ethereum completed The Merge, officially switching to Proof of Stake. Mining was removed, and block production is now handled by validators who lock up ETH as collateral. If they misbehave, part of their stake can be slashed.
Beyond Ethereum, several major networks also use PoS like:
- Cardano applies the Ouroboros protocol with stake pools and delegation.
- Avalanche uses AVAX staking and the Avalanche family of consensus protocols to finalize blocks quickly.
- Polkadot and Tezos adopt their own PoS variants (Nominated PoS and liquid PoS) to secure validators and reward token holders who delegate stake.
Delegated Proof of Stake (DPoS)
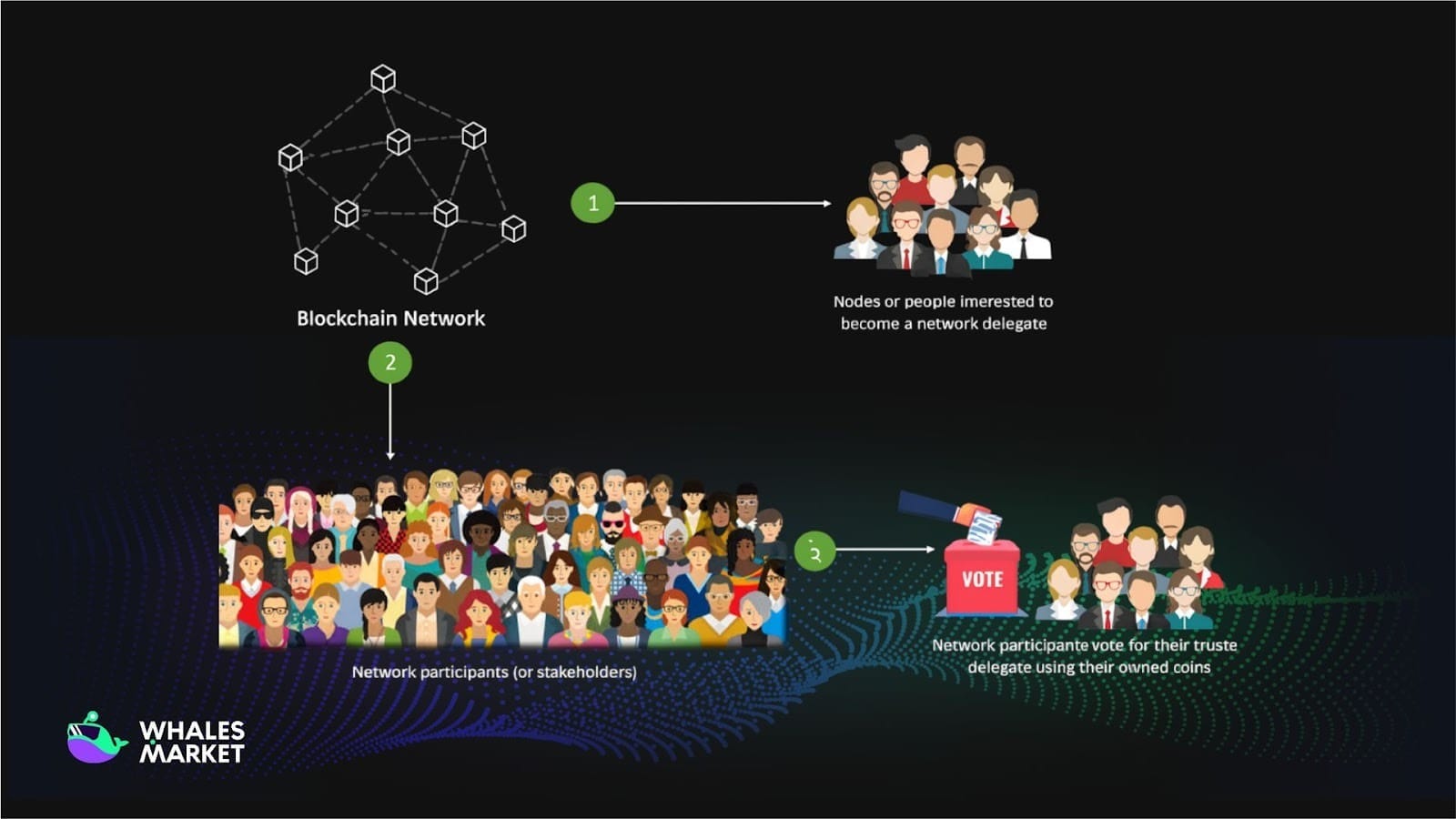
DPoS is a variant of PoS, where users vote to select a group of delegates to represent them in validating transactions. These delegates take turns creating and confirming blocks based on the votes received. If a delegate is dishonest, they can be replaced through subsequent voting. This system resembles representative democracy in blockchain.
Advantages:
- High speed and ability to handle thousands of transactions per second (like EOS or Tron).
- Resource-efficient, easy to scale for large networks.
- Increases democracy through voting mechanisms, reducing manipulation risks.
Disadvantages:
- Can lead to power concentration in a small group of delegates, resembling an oligarchy.
- Risk of bribery or collusion among delegates.
- Less decentralized than pure PoW or PoS, as it depends on selected delegates.
EOS and Tron are two of the most well-known blockchains that adopt Delegated Proof of Stake.
Proof of Authority (PoA)
PoA relies on the identity and reputation of pre-authorized nodes. Only a small group of trusted nodes (often verified organizations or individuals) are allowed to validate blocks. They take turns signing blocks based on identity, and if they violate rules, their identity is affected, leading to loss of rights.
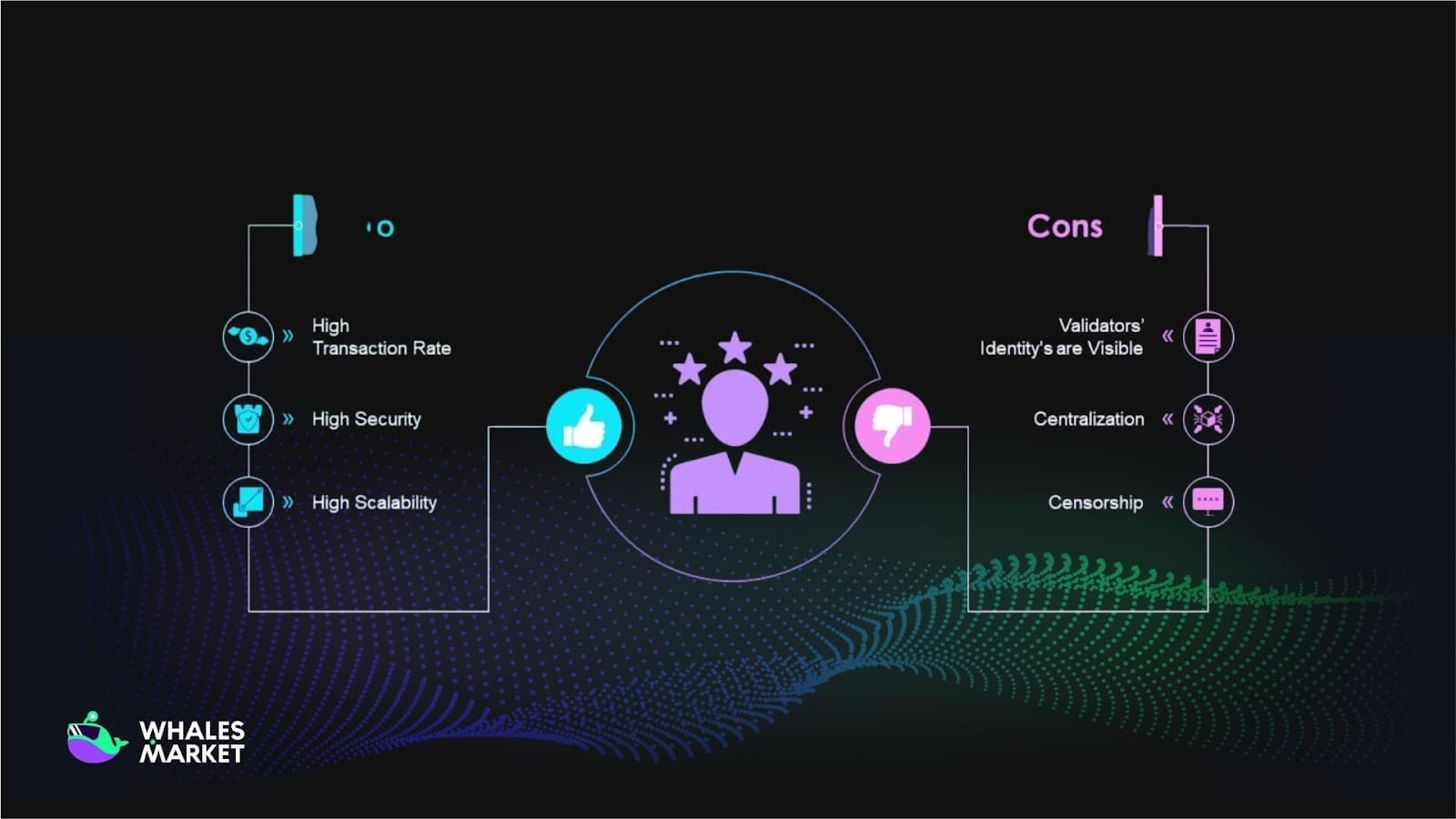
Advantages:
- Offers fast performance and high energy efficiency, suitable for private networks (like VeChain).
- Good security in controlled environments with low fault tolerance.
- Easy to manage and deploy for enterprises.
Disadvantages:
- Less decentralized, dependent on centralized nodes, easily criticized as not truly decentralized.
- High risk if authorized nodes are hacked or colluded.
- Not suitable for public blockchains due to lack of openness.
Some blockchains that use Proof of Authority include VeChainThor and the early version of Gnosis Chain. They rely on a small set of approved validators to produce blocks, which allows fast confirmation times and predictable network performance.
PoH (Proof of History)
PoH (Proof of History) is not an independent consensus mechanism as many people mistakenly believe, but a supporting tool, also known as a pre-consensus tool, that optimizes the process of reaching consensus in the Solana blockchain network.
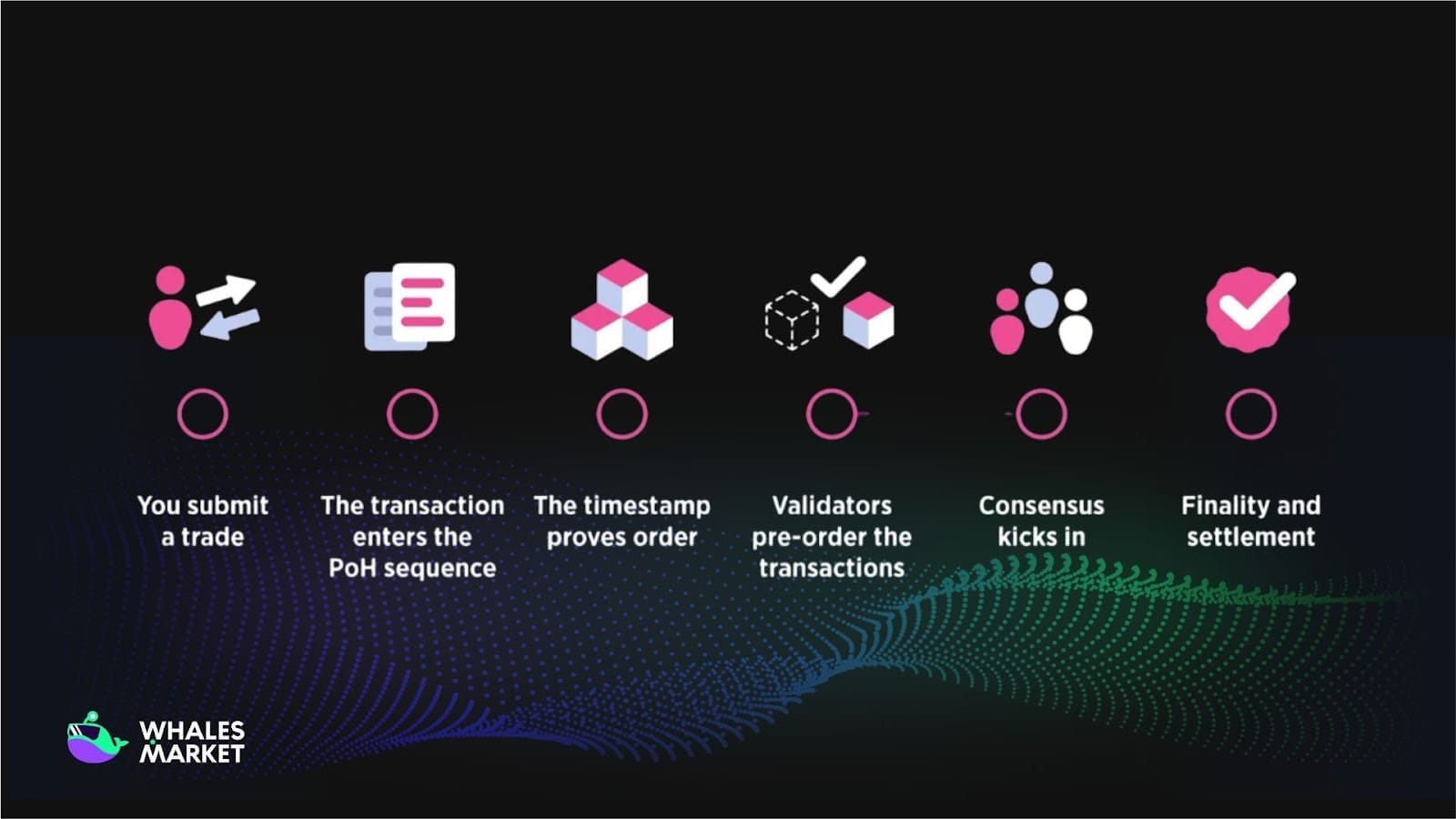
It functions as a decentralized clock that allows nodes in the network to agree on the order and timing of events without constant communication or relying on a centralized clock. This reduces latency and increases transaction processing speed.
How PoH works in a simple way:
- PoH uses a Verifiable Delay Function (VDF) combined with the SHA-256 hashing algorithm to generate a continuous chain of hashes. Each hash depends on the previous hash, input data, and the actual time that has passed.
- The block producer, also called the validator, calculates this VDF to prove that a certain amount of time has passed since the previous proof. It cannot be faked because recalculating the entire chain would be very time-consuming.
- The result is a verifiable historical timeline embedded directly into the blockchain, allowing nodes to validate quickly and in parallel rather than sequentially like many other blockchains.
How PoH contributes to Solana:
- It does not replace Solana’s actual consensus mechanism, which is Tower BFT, a variation of Byzantine Fault Tolerance combined with Proof of Stake.
- Instead, PoH supports the network by providing reliable timestamps, helping reduce energy consumption, unlike Proof of Work, increasing throughput to thousands of transactions per second, and improving scalability without requiring sharding from the beginning.
- For example, while Proof of Work like Bitcoin uses energy to solve puzzles, and Proof of Stake like Ethereum uses stake to select validators, PoH is only a supporting layer that makes consensus faster and more secure without requiring many resources.
Others
Additionally, the market has witnessed some less common and rare consensus mechanisms, such as:
- Sui uses a flexible consensus model based on Delegated Proof of Stake (DPoS), combined with advanced Byzantine Fault Tolerant (BFT) protocols like Mysticeti. This allows parallel processing of transactions, distinguishing between simple and complex transactions.
- Aptos employs AptosBFT, a variant of Byzantine Fault Tolerance based on HotStuff, combined with Proof of Stake (PoS) to ensure safety and efficiency. It focuses on parallel execution and modular design to outperform monolithic chains.
- Proof of Burn (PoB): Proof of Burn is a consensus mechanism where users "burn" (destroy) cryptocurrency to prove commitment and earn validation rights. It is designed to mimic the cost of Proof of Work with much lower energy use, while increasing scarcity and making spam attacks more expensive.
- Proof of Capacity (PoC):Proof of Capacity is a consensus mechanism that uses hard drive space instead of CPU power or staking, where miners pre-compute and store “plots” of data to participate in block creation. It is considered more energy-efficient and accessible, but it requires significant storage capacity, plotting time, and careful management of storage-related risks.
In summary, choosing a consensus algorithm depends on the blockchain's goals, such as prioritizing security, speed, or energy efficiency. These consensus mechanisms are continuously evolving to overcome drawbacks, and no type is absolutely perfect.
Conclusion
Hopefully, through this article, you have gained an overview of what a Blockchain Consensus Mechanism is and classified most of the mechanisms currently available on the market.
FAQs
Q1. How does consensus affect transaction finality on a blockchain?
Consensus determines when a block is considered irreversible. In PoW, finality increases as more blocks are added after it, while PoS and PBFT-style systems often provide faster or immediate finality once validators agree.
Q2. Can a blockchain operate without a consensus mechanism?
No. Without consensus, nodes would not know which version of the ledger is correct, leading to conflicting transaction histories, double spending, and loss of trust.
Q3. What happens if two blocks are proposed at the same time?
This creates a temporary fork. Nodes follow the consensus rules to decide which block becomes canonical. The other block is eventually discarded, and its transactions return to the mempool.
Q4. Is consensus only needed for public blockchains?
No. Private and enterprise blockchains also require consensus to ensure reliability, coordination, and fault tolerance among participants, even if they already trust one another.
Q5. Why do some consensus mechanisms consume less energy than others?
PoW relies on computational competition, requiring large electricity usage. PoS, PoA, PBFT, reduce or remove that competition, so they validate blocks with far lower energy consumption.