A Private Key acts as the master key that determines true ownership of a crypto wallet. Once it is lost, the assets are permanently gone, with no recovery and no one able to help. This article explains clearly what a Private Key is, how it works, how to protect it, and the critical mistakes that must be avoided.
What Is a Private Key in Crypto?
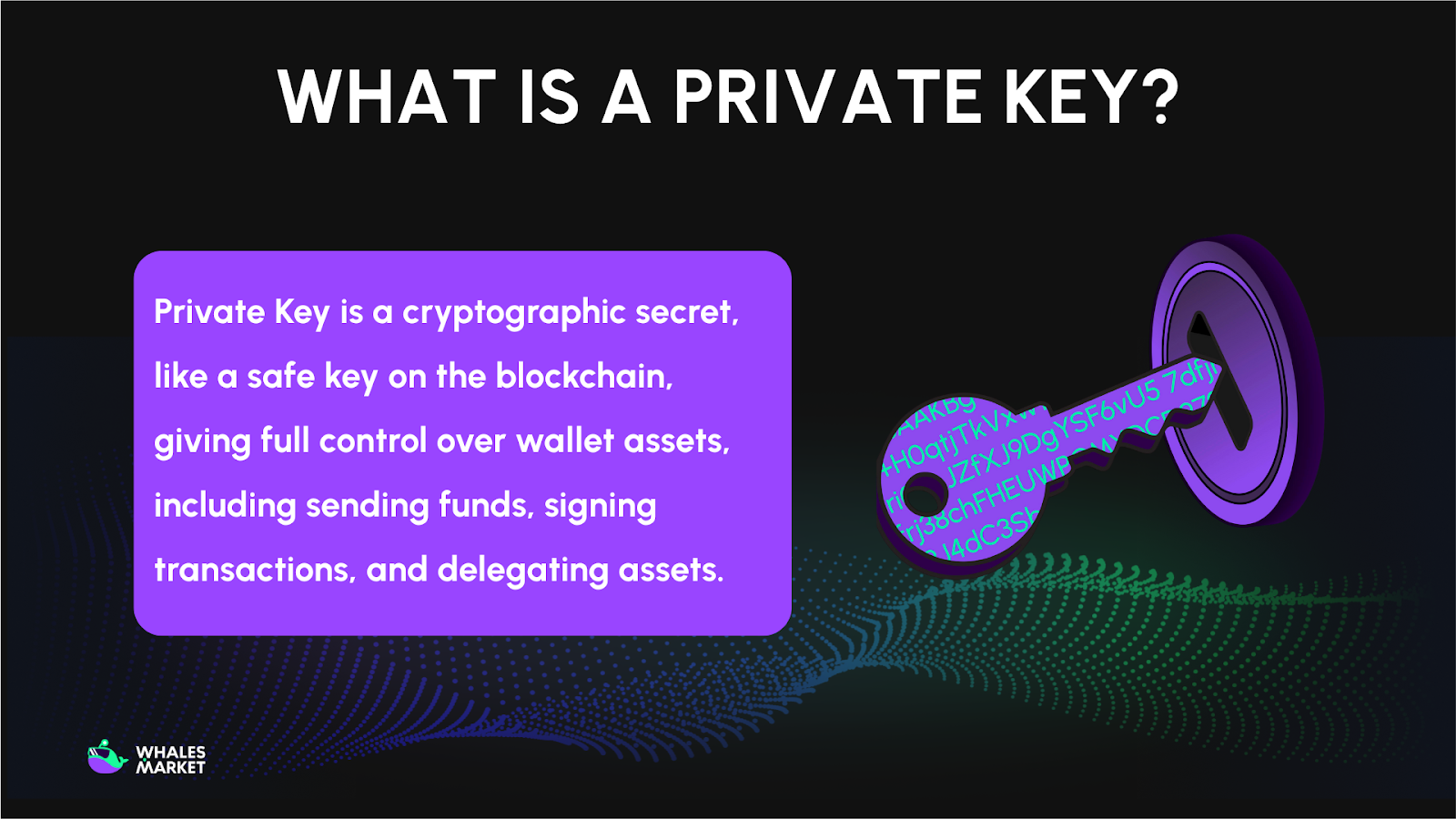
Private key is a secret string of characters generated through cryptographic algorithms. In simple terms, it functions like the original key to a safe on the blockchain network. Whoever holds the private key has full control over the assets in the corresponding wallet, including the right to send funds, sign transactions, and delegate assets.
The most important point to remember is this: Blockchain does not recognize personal names or identities. Ownership of cryptocurrency is not tied to a name, email, or phone number. It depends on one thing only, the private key.
In other words:
- Whoever holds the private key is recognized by the blockchain as the owner.
- Losing a private key means losing access forever.
- If another person has the private key, they can transfer all assets, even if those assets do not belong to them in the real world.
The concept of the private key comes from asymmetric cryptography, a field studied since the 1970s. Its core principles include:
- One secret key, the private key, used to sign.
- One public key used to verify.
Private keys only became widely known after 2009, when Bitcoin was introduced. For the first time, blockchain made it possible for:
- Users to directly own their assets.
- Ownership without banks, intermediaries, or centralized authorities.
Bitcoin uses the ECDSA digital signature algorithm with the secp256k1 elliptic curve, enabling extremely secure private keys while still processing transactions fast enough at a global scale.
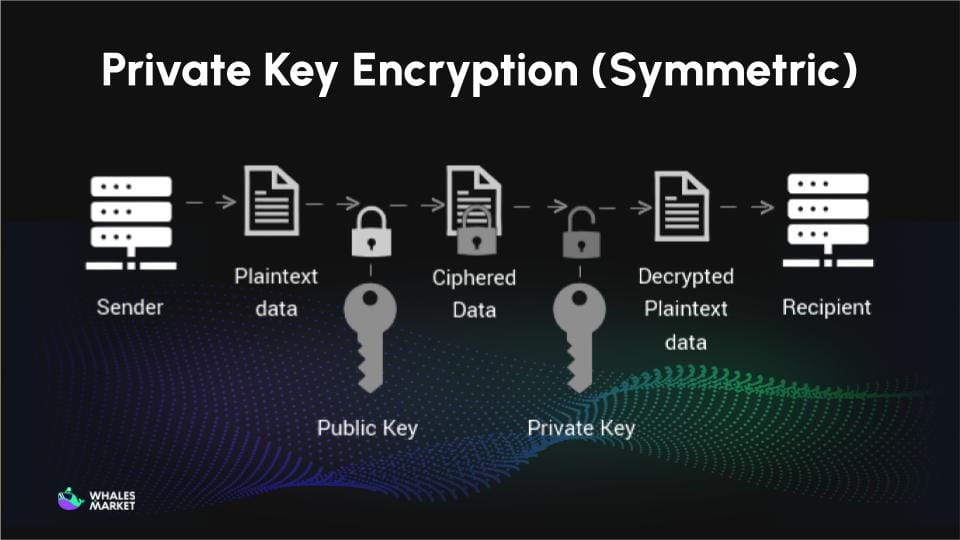
How does Public & Private Key encryption work?
A private key operates under asymmetric encryption, a system that uses a key pair with a one-way mathematical relationship. The process of creating a wallet (including private versus public keys) through asymmetric encryption and transaction signing is as follows.
Step 1: Generating a private key: When a new crypto wallet is created, the system randomly generates a 256-bit integer from a high-quality entropy source. This number is the private key. Example of a hex-format private key with 64 characters:
f3c8f9a6198cca98f481edde13bcc031b1470a81e367b838fe9e0a9db0f5993d
Step 2: Deriving the public key: The private key is multiplied by a fixed generator point G on the secp256k1 elliptic curve to produce the public key.
Formula: Public Key = Private Key × G
This operation relies on the Elliptic Curve Discrete Logarithm Problem, which cannot be solved within a reasonable time using current technology.
Step 3: Creating the wallet address: The public key is hashed using SHA-256 and RIPEMD-160 to generate a shorter wallet address:
- Bitcoin addresses start with 1, 3, or bc1
- Ethereum addresses start with 0x and are 42 characters long
- Solana addresses use Base58 and are 32 to 44 characters long
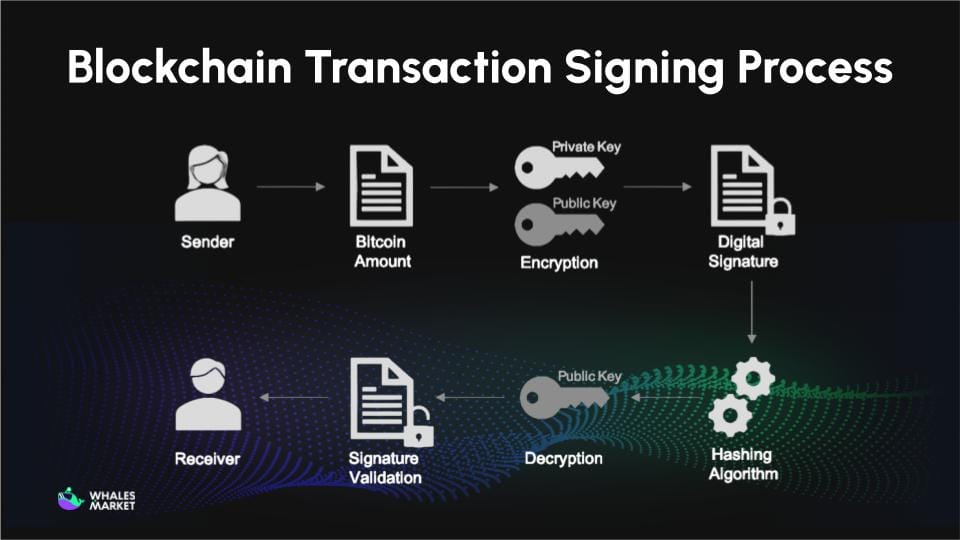
Step 4: Signing transactions: Whenever crypto is transferred, the private key creates a digital signature that proves legitimate ownership. The signing process works as follows:
- A transaction is created, such as “Transfer 1 ETH from wallet A to wallet B”
- The transaction is hashed into a unique fingerprint
- The private key signs this hash using ECDSA
- The transaction and signature are broadcast to the network
- Nodes verify the signature using the public key
- If valid, the transaction is permanently recorded on the blockchain
The key point is that the private key is never transmitted. Only the signature is broadcast, so even if someone intercepts the transaction, the private key remains unknown.
Key Properties of a Private Key in Crypto
- Uniqueness: Each private key is generated randomly within a 2²⁵⁶ key space, making collisions virtually impossible and ensuring every wallet is unique.
- Immutability: A private key is created only once at wallet initialization and cannot be changed. If it is suspected to be compromised, a new wallet must be created and assets transferred.
- One-way function: A private key can easily generate a public key and address, but it is computationally impossible to reverse from an address back to the public key.
- Self-custody: Blockchain provides no recovery mechanism. The holder of the private key has full control and full responsibility for security.
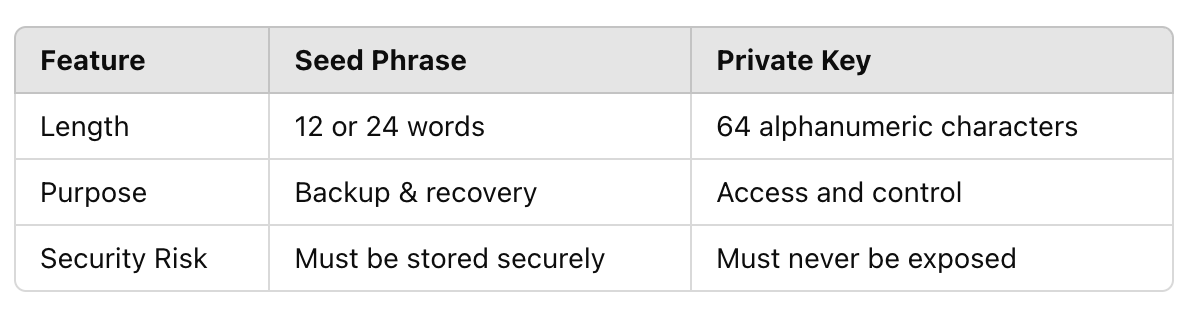
Difference between Private Key vs Seed Phrase
This is one of the most confusing concepts for newcomers. Seed phrase and private key are closely related but not identical.
A seed phrase, also known as a recovery phrase or mnemonic, consists of 12 or 24 English words generated when a wallet is created. The seed phrase is essentially a human-readable representation defined by the BIP39 standard since 2013.
Example of a 12-word seed phrase: legal winner thank year wave sausage worth useful legal winner thank yellow
In simple terms, the seed phrase acts like the master key of a building. From it, many individual room keys can be generated. Each room key represents a specific private key.
Why Can’t Anyone Hack a Private Key?
If a private key is just a number, why not try every possible combination? The answer lies in mathematics.
The total number of possible private keys is 2²⁵⁶, written in full as:
115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936
That is a 78-digit number. For comparison:
- Estimated number of atoms in the observable universe: ~10⁸⁰
- Estimated number of grains of sand on Earth: ~10²³
- Possible private keys: ~10⁷⁷, nearly the number of atoms in the universe
Assume a supercomputer can test 10¹² private keys per second.
- Time required: 3.67 × 10⁵⁷ years
- Age of the universe: ~13.8B years
This means it would take about 10⁴⁷ times the age of the universe to try all combinations.
Conclusion: Attempting to guess a private key by systematically testing every possible combination is impossible with any current or foreseeable technology.
Billions Lost Due to Private Keys. Why?
If private keys are mathematically secure, why are billions of dollars still lost? The answer is simple. The problem lies with humans, not algorithms.
Common reasons for private key loss:
- Phishing: Users are directed to fake wallet, exchange, or airdrop websites and voluntarily enter their private key or seed phrase. The blockchain treats these transactions as valid, so assets are transferred immediately and cannot be recovered.
- Malware and keylogger: Infected devices can record keystrokes, clipboard data, or screen activity, allowing private keys to be stolen without the user noticing until the wallet is completely drained.
- Unsafe storage: Seed phrases are photographed, stored in cloud services, or saved in note apps, increasing the risk of exposure when email, phone, or cloud accounts are compromised.
- Social engineering: Attackers impersonate administrators, support staff, or moderators and use psychological pressure and false information to trick users into revealing seed phrases.
- Supply chain attacks: Purchasing second-hand or unverified hardware wallets can result in private keys being pre-known or devices being shipped with malicious firmware.
Statistics consistently show that exposed private keys rank among the top causes of crypto-related losses.
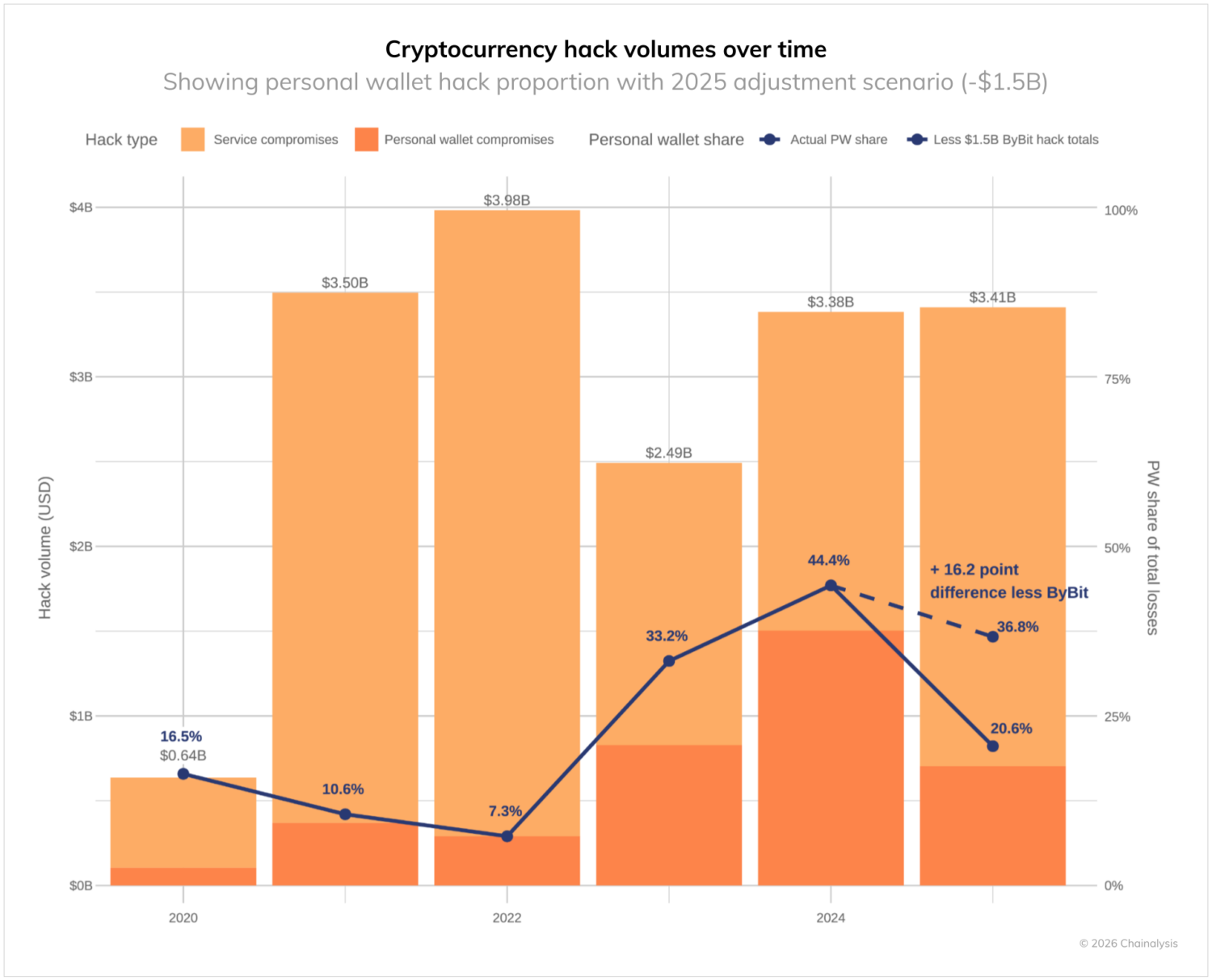
Based on the data shown in Chainalysis Report, hacks linked to personal wallet compromises, often driven by exposed private keys, account for roughly $1.2B in losses in 2025, representing about 35%–40% of total crypto hack volume that year.
How to protect Private Key in Crypto
Most people who lose crypto do not fail due to lack of technical knowledge. They fail because they believe it will never happen to them. Private keys are secure by design, but one careless decision can nullify every layer of protection.
In crypto, there is no second line of defense. The private key is the final layer.
Security starts with accepting inconvenience
Real security begins with accepting inconvenience. Writing a seed phrase on paper or engraving it on metal, storing copies in multiple locations, avoiding photos and cloud storage, may feel cumbersome. That inconvenience is the cost of self-sovereignty.
Any solution that feels more convenient is usually trading safety for risk, sooner or later.
Hardware wallets follow the same logic. Plugging in a device, reading the screen, and confirming transactions may slow things down by a few seconds. In return, the private key never leaves the device. That slowness is protection, not a weakness.
Small inconvenience can prevent massive losses.

Do not use one wallet for everything
A common mistake is using one wallet for all activities: trading, long-term holding, testing new dApps, signing airdrops, and connecting unknown links.
Separating wallets by purpose is one of the most effective security practices. Many avoid it because managing multiple wallets feels tiring. When a wallet is compromised, separation limits damage instead of exposing all assets.
A hardware wallet is not a magic shield
Hardware wallets are not perfectly safe on their own. They protect against malware and keyloggers, but they cannot stop users from entering seed phrases on fake websites or signing malicious transactions without carefully reading on-screen details. A device is only as secure as the discipline of its user.
Testing wallet recovery is rare but critical
One simple step is often skipped: testing wallet recovery.
Many users write down a seed phrase incorrectly or in the wrong order without realizing it. Only when recovery is needed does the mistake become apparent, and by then it is too late. Creating a wallet, deleting it, and restoring it before depositing large amounts ensures the Seed Phrase is accurate and complete.
Conclusion
“Your Keys, Your Coins. Not Your Keys, Not Your Coins.” Blockchain technology is secure, but a single careless moment can lead to permanent loss. Proper understanding, correct storage, and strict discipline are the only ways to protect assets.
FAQs
Q1: What does a private key look like?
A private key usually looks like a long, random string of letters and numbers. It may appear as plain text, a QR code, or be hidden behind a wallet interface to keep it secure. Private key example: f3c8f9a6198cca98f481edde13bcc031b1470a81e367b838fe9e0a9db0f5993d
Q2: Which is more important, the Private Key or the Seed Phrase?
Both are equally important. The seed phrase is a backup that can regenerate all private keys in a wallet. Losing either means losing complete control of assets, with no recovery or third-party intervention.
Q3: Can a Private Key be changed?
No. A private key is created once during wallet initialization and is permanently tied to that address. If it is exposed or suspected to be unsafe, the only solution is to create a new wallet and transfer all assets.
Q4: Do exchanges store Private Keys?
Yes. When assets are deposited into an exchange, control of the private keys is handed over to the platform. Users only control an internal account, while the on-chain assets are managed by the exchange.
Q5: What is the primary use of a private key?
Not at present. Quantum computers capable of breaking ECDSA do not yet exist in practice. Before such a threat becomes real, major blockchains are expected to migrate to quantum-resistant algorithms.
Q6: Where is the Private Key stored on the blockchain?
A private key is never stored on the blockchain. It exists only where the user keeps it, such as on personal devices or written as a seed phrase. The blockchain stores only wallet addresses and valid signed transactions, never private keys.

