Crypto theft no longer looks like a hack. There are no breached servers, no broken smart contracts, and often no obvious warning signs. In many cases, a single wallet signature is all it takes for assets to disappear permanently.
The scale of crypto phishing attack has reached alarming levels. In 2024, phishing-related attacks drained roughly $500M, affected over 332,000 wallet addresses, and pushed total losses up 67% year over year. In first half of 2025, scams and hacks already caused $3.1B in losses, with phishing and social engineering accounting for $594.1M. Understanding how crypto phishing works is no longer optional, it is a basic requirement for surviving in this ecosystem.
What Is a Crypto Phishing Attack?
Crypto phishing attack is a type of scam that targets cryptocurrency users with the goal of stealing assets directly from their wallets. Unlike traditional phishing attacks, which usually focus on email passwords or bank accounts, crypto phishing scams are more sophisticated because they exploit the unique mechanics of blockchain and DeFi systems.

A common scenario looks harmless at first. A user sees an attractive airdrop announcement on X, clicks the link, connects a MetaMask wallet, and signs a transaction to “claim free tokens.” Within seconds, all tokens and NFTs in the wallet disappear. This is a typical crypto phishing attack.
Why is Crypto Phishing Attack more dangerous?
Crypto phishing attacks are often more dangerous than traditional phishing because blockchain transactions are irreversible, attackers remain anonymous, and a single wallet signature can result in permanent asset loss.
- Irreversible transactions: Blockchain transactions are final once confirmed. There is no central authority, bank, or support team that can freeze, cancel, or reverse a transfer after it has been executed on-chain.
- Attacker anonymity: Stolen funds can be moved instantly through mixers and cross-chain bridges, making attackers extremely difficult to identify or trace once laundering begins.
- One signature is enough: A seed phrase does not need to be exposed. Signing a single malicious approval or permit can grant attackers ongoing access to wallet assets.
- No insurance or compensation: Most crypto platforms do not reimburse phishing-related losses. Once assets are stolen, recovery is rare and usually impossible.
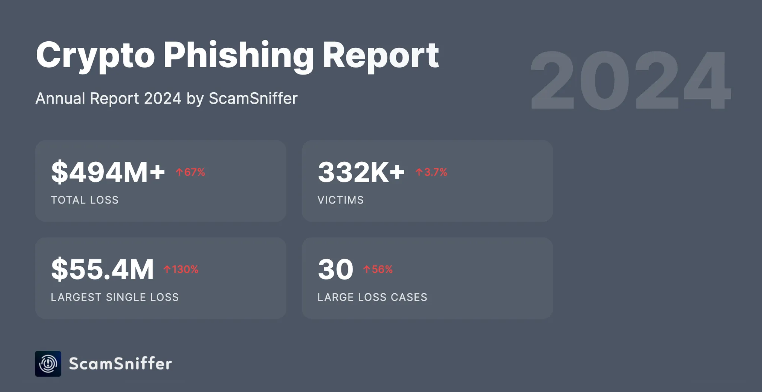
In 2024, wallet drainer attacks (a kind of crypto phishing attack) accounted for approximately $500M in stolen assets, according to Scam Sniffer.
- Around 332,000 wallet addresses were affected by phishing-related incidents.
- Total losses increased by 67% compared to 2023.
- The largest single transaction theft reached $55.48M.
- There were 30 large-scale thefts, each exceeding $1M.
- Losses from phishing signature attacks alone totaled $790M.
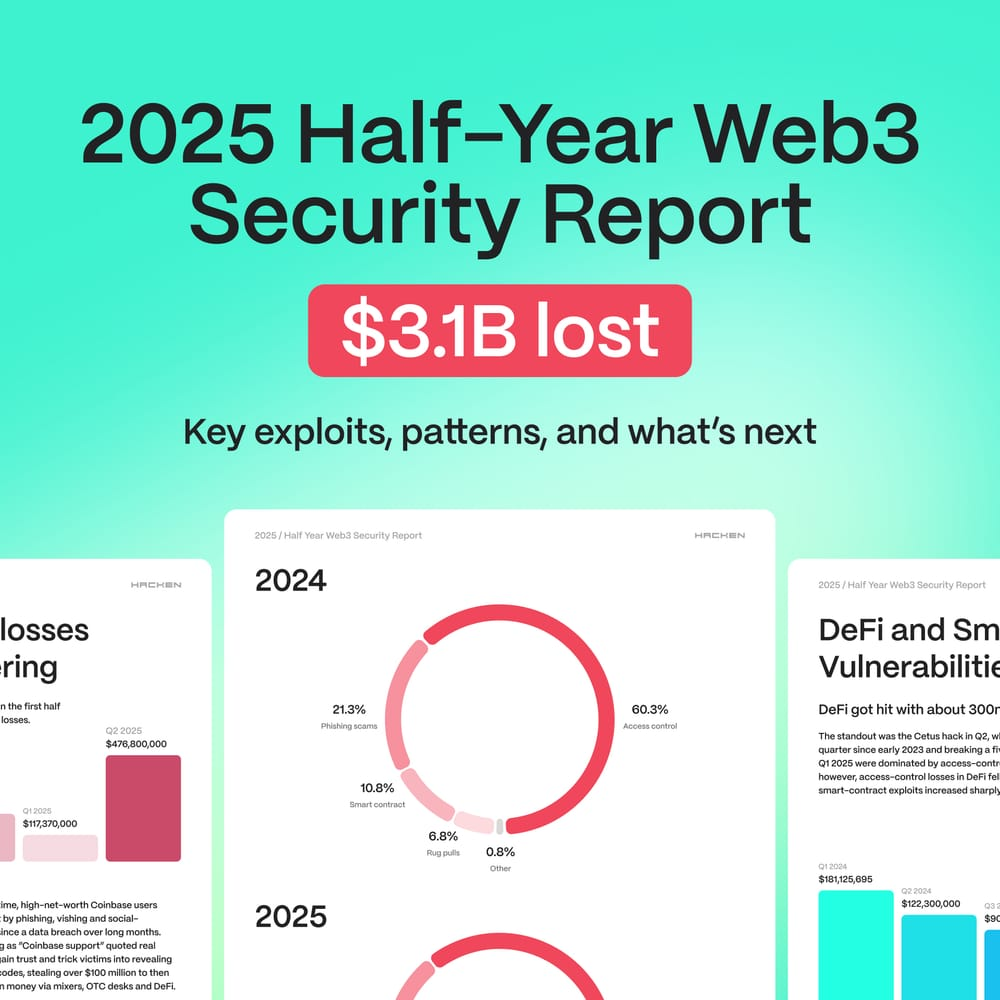
In the first half of 2025, according to reports from Chainalysis, Hacken, and other cybersecurity firms:
- $3.1B was lost to scams and hacks in the first six months of the year, with projections exceeding $4.3B for the full year.
- Phishing and social engineering accounted for $594.1M of total losses.
- The Bybit hack in February 2025 resulted in $1.5B stolen, marking the largest crypto theft in history.
- Address poisoning attacks affected 17M victims and caused losses of $83.8M.
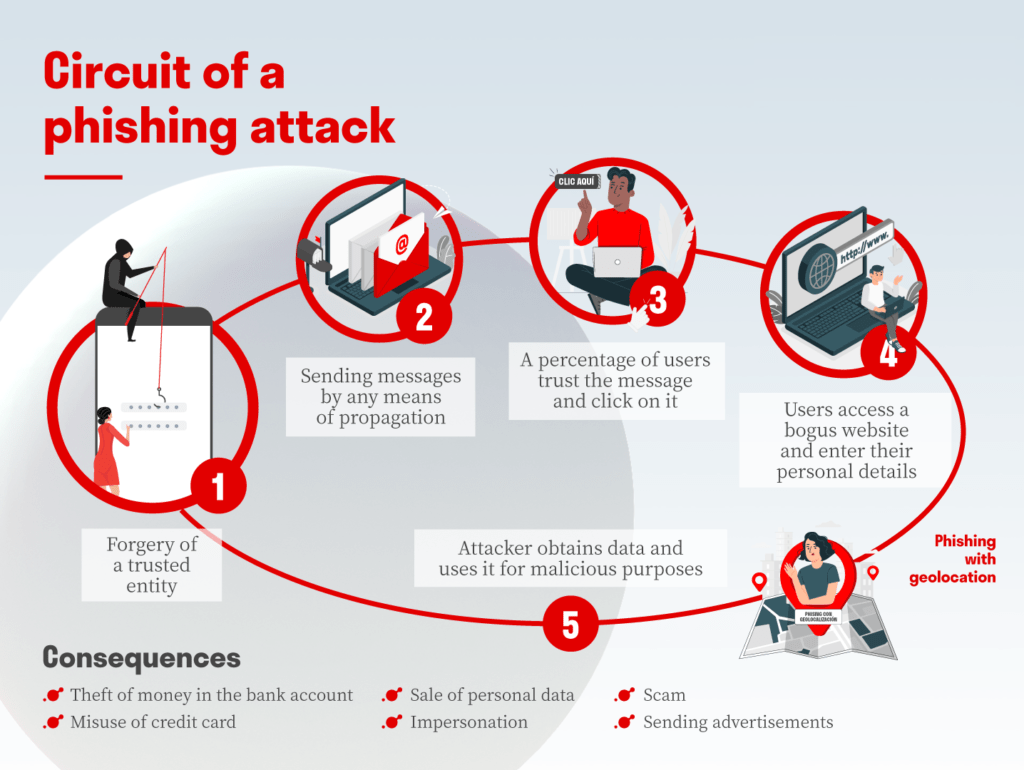
How does a phishing attack work in Crypto?
Crypto phishing attacks follow a predictable pattern designed to exploit trust and wallet permissions. Understanding each step helps users recognize threats before assets are compromised.
- Step 1 (Impersonation): Scammers impersonate trusted entities such as wallets, exchanges, airdrop campaigns, or official support teams to gain credibility.
- Step 2 (Distribution): Phishing messages are distributed through emails, Telegram, Discord, Twitter/X, fake advertisements, or “wrong number” messages.
- Step 3 (Trust & Engagement): Users trust the message due to FOMO or fake security alerts and click the provided link.
- Step 4 (Fake Interface): Victims are redirected to a fake website or dApp and prompted to connect their wallet, sign a transaction, or enter sensitive information.
- Step 5 (Asset Drain): Once a malicious approval or signature is granted, attackers drain assets from the wallet almost instantly.
Common Types of Phishing Scam in Crypto
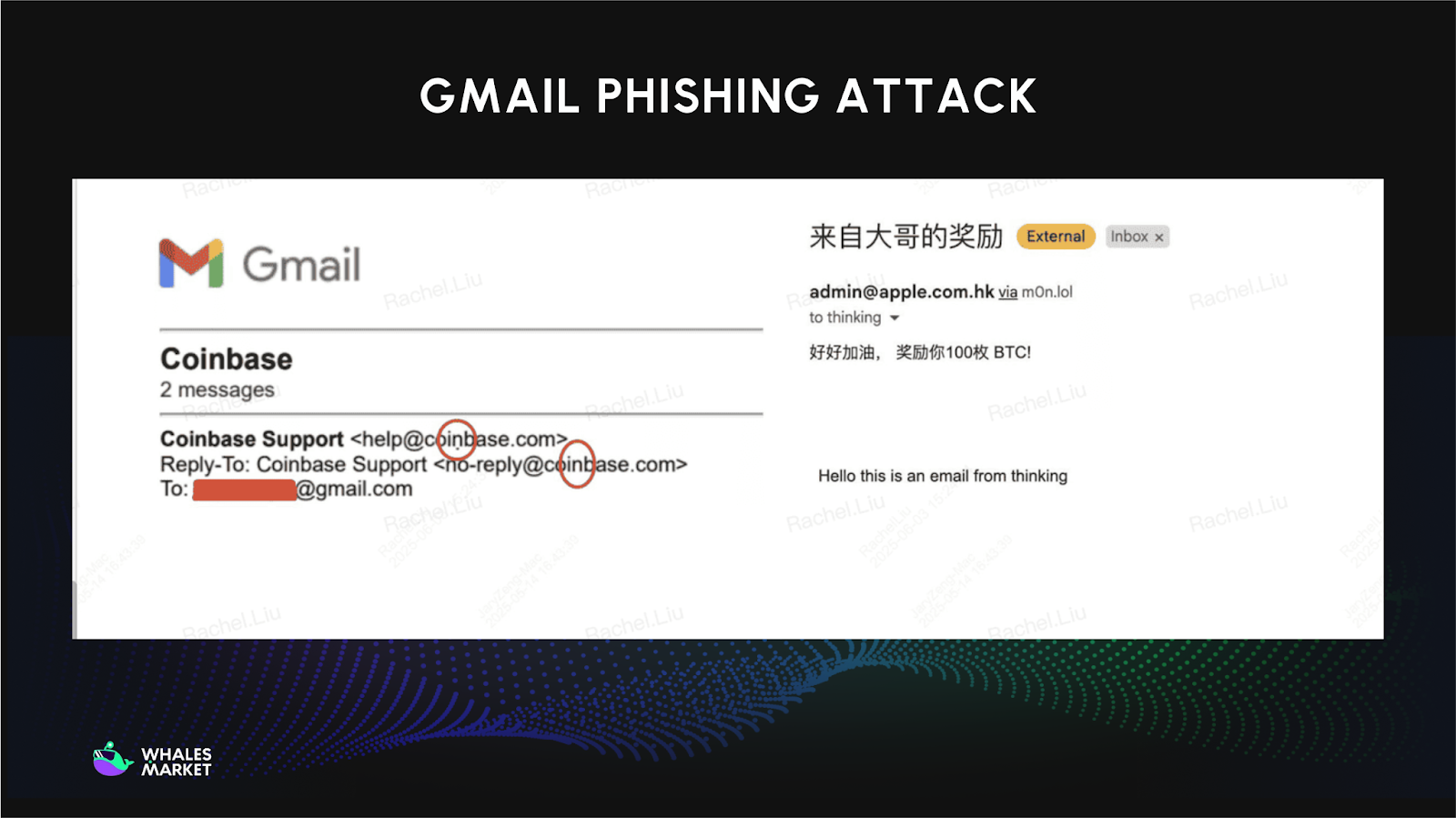
Gmail Phishing Attack
Gmail phishing attack remains one of the most effective phishing channels in crypto because it is easy to fake legitimacy. Attackers copy logos, brand colors, writing style, and even spoof sender names to look like official exchange notifications.
These mails usually create urgency, claiming suspicious logins, failed withdrawals, or account verification issues. Victims are directed to a fake login page where passwords, 2FA codes, or recovery details are harvested. Once credentials are entered, accounts are often drained within minutes.
Security reports consistently show email phishing as the primary entry point for crypto account compromises, largely because users trust familiar-looking emails and act quickly under pressure.
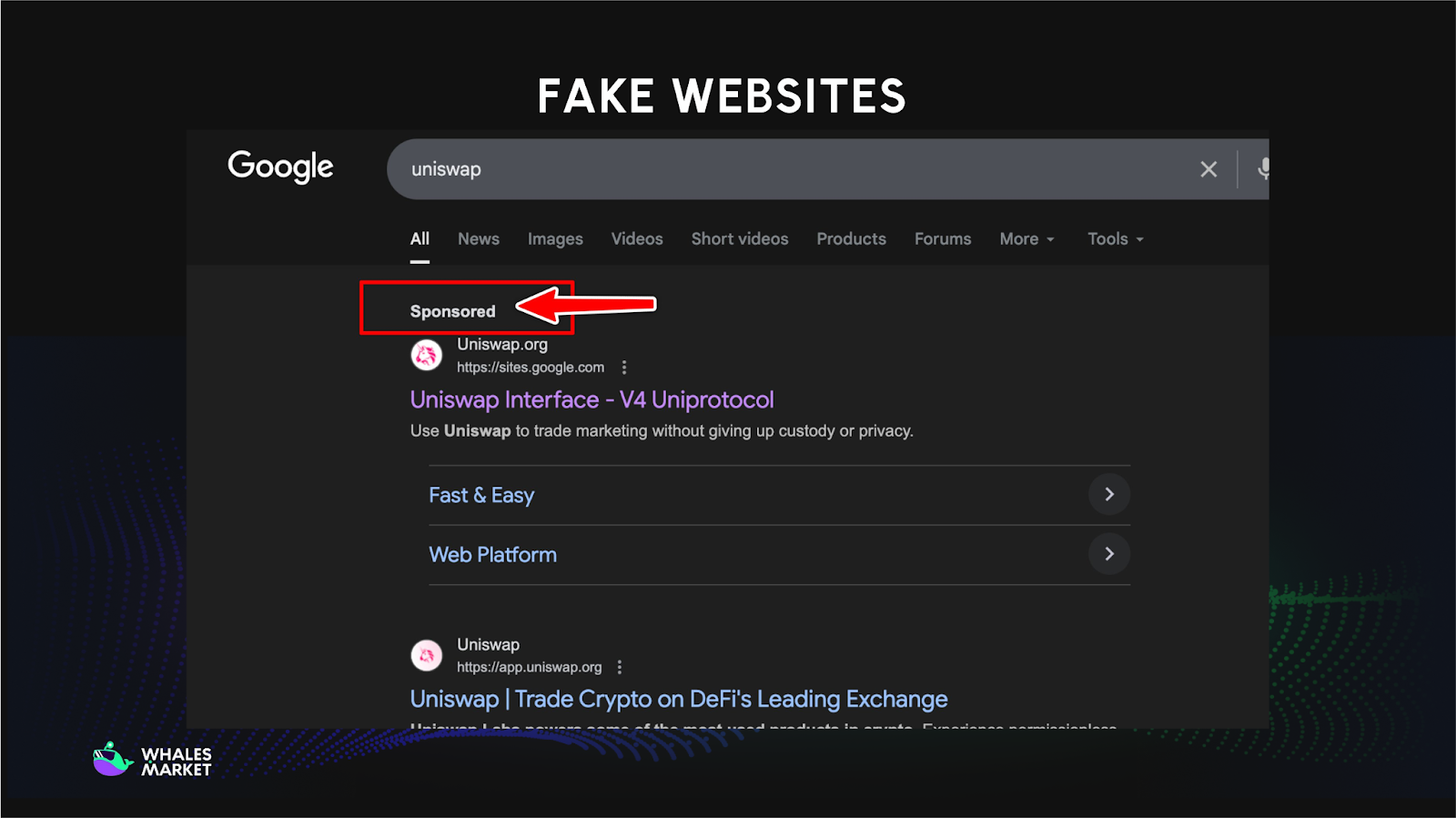
Fake Websites
Fake websites are designed to look nearly identical to legitimate exchanges or wallet interfaces. Attackers often register domains that differ by just one character or use visually similar letters, making them difficult to detect at a glance.
Once users enter login credentials, seed phrases, or 2FA codes, attackers gain full control of the wallet or exchange account. Some fake sites even simulate real wallet pop-ups to trick users into approving malicious transactions.
Academic research and on-chain analysis have shown that URL impersonation and cloned interfaces are responsible for tens of millions of dollars in losses across major blockchains.
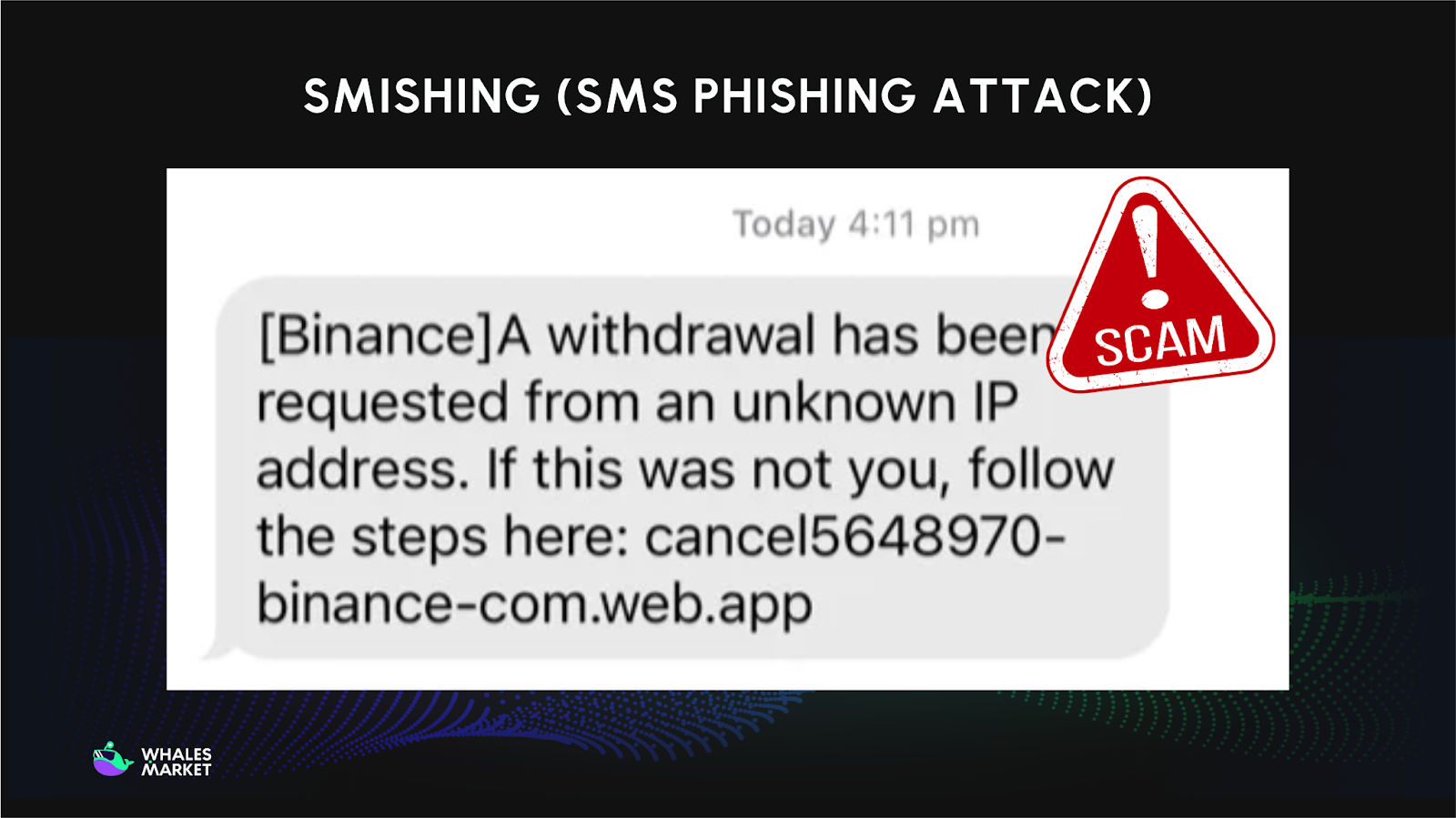
Smishing (SMS Phishing Attack)
Smishing (SMS Phishing attack) uses text messages to create fear or urgency, pushing users to act quickly without verification. Messages may claim account suspension, failed withdrawals, or eligibility for exclusive airdrops.
These texts usually include shortened URLs that redirect to malicious websites designed to steal credentials or wallet approvals. Mobile alerts feel more urgent than emails, which makes users more likely to react immediately.
Attackers rely on speed and emotional response rather than technical sophistication. The moment a user clicks the link, the scammer gains an opportunity to compromise the account.
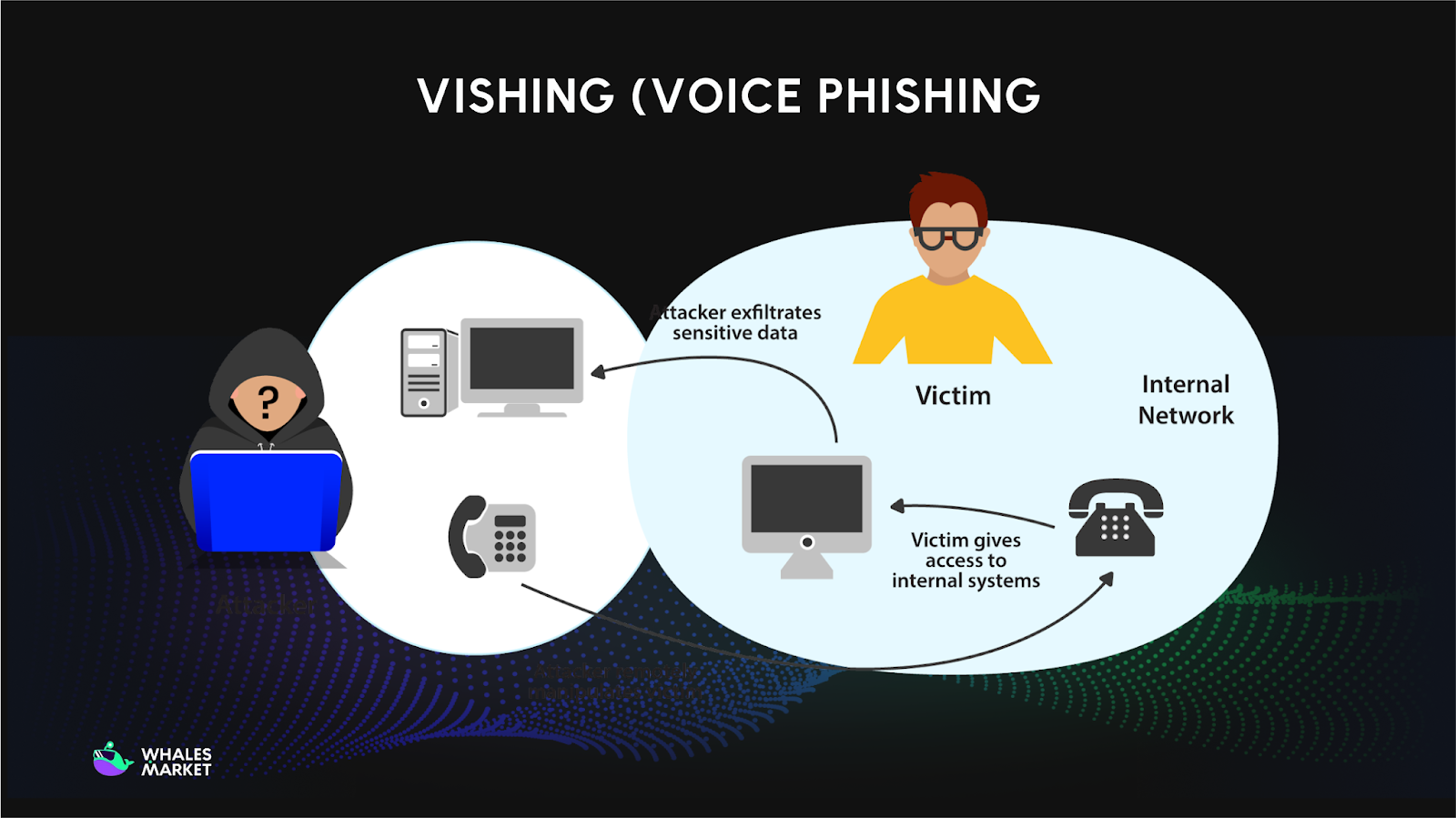
Vishing (Voice Phishing Scam)
Vishing (Voice Phishing attacks) occur through phone calls where scammers impersonate exchange support staff, security teams, or even banks. They claim urgent issues and request sensitive information such as passwords, 2FA codes, seed phrases, or remote access.
With AI voice cloning, these calls now sound highly realistic, sometimes mimicking official support agents or even people the victim knows. This realism increases trust and lowers suspicion.
Security reports show that voice-based social engineering remains one of the most effective attack methods in crypto, especially when combined with urgency and authority.
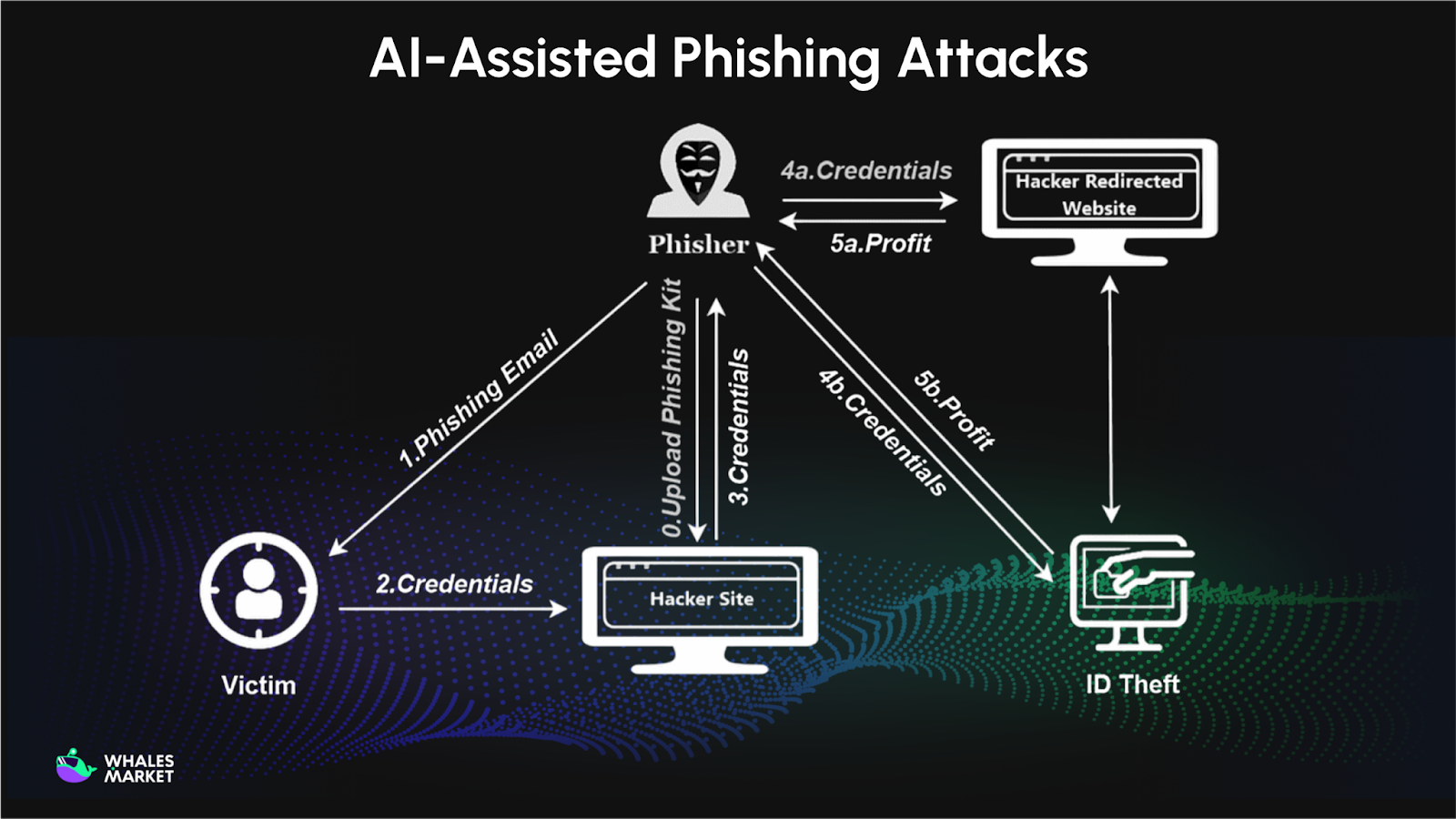
AI-Assisted Phishing Attacks
AI has dramatically increased the effectiveness of phishing scams. Attackers now use chatbots, voice cloning, and deepfake videos to mimic real customer support interactions in real time.
These tools allow scammers to personalize messages using leaked data, respond instantly, and maintain convincing conversations. Some attacks even include fake anti-phishing codes or security warnings to build trust.
According to blockchain crime reports, AI-assisted phishing attack has significantly increased total scam revenue by enabling large-scale, highly believable attacks.
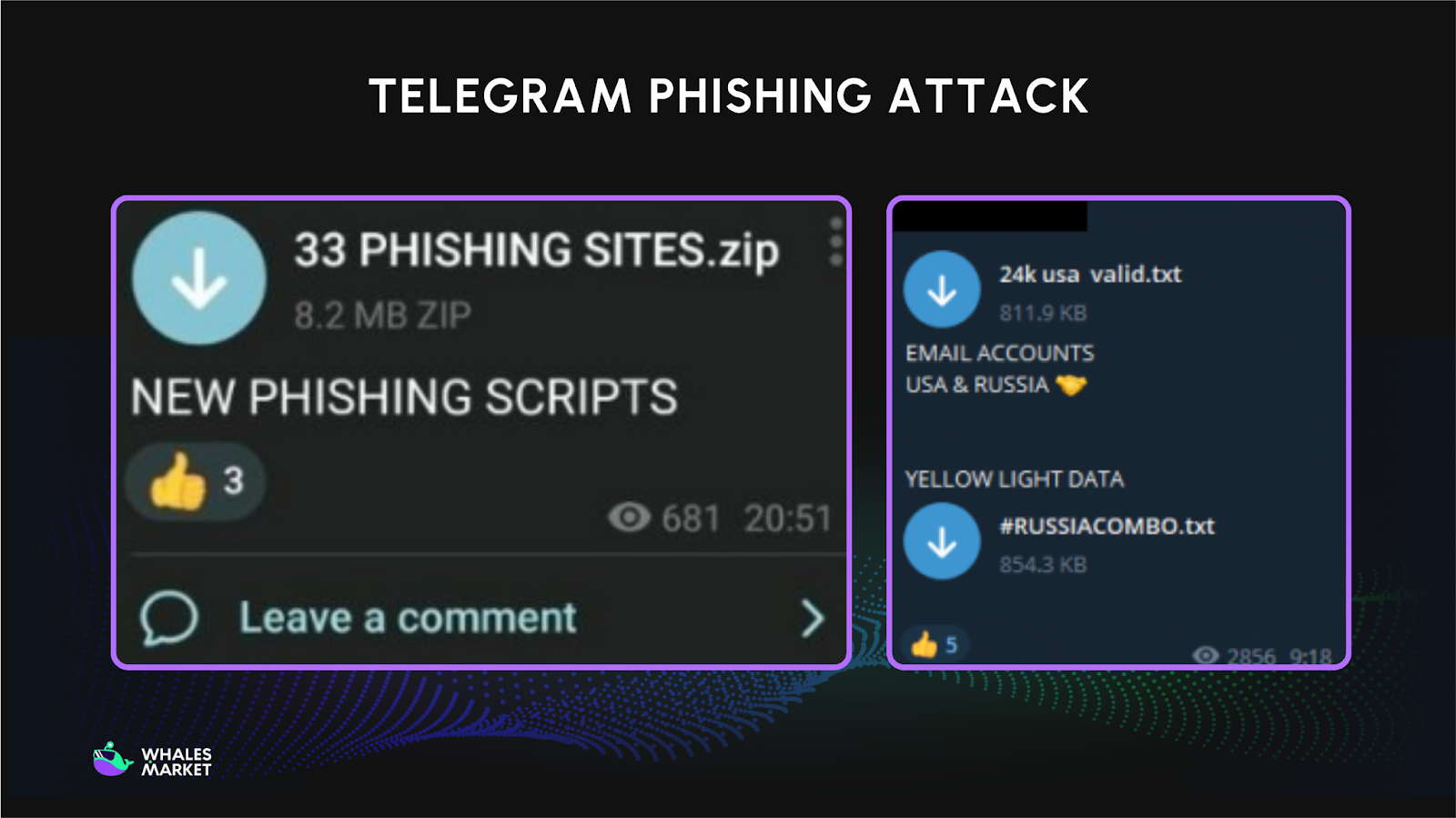
Telegram Phishing Attack via Fake Bots and Admins
Telegram is a major hub for crypto communities, making it a prime phishing target. Scammers create fake support bots or impersonate project admins to contact users directly.
Typical scams involve claims of deposit errors, KYC problems, or withdrawal issues, followed by requests for seed phrases or links to fake support portals. Once credentials are shared, funds are usually stolen within minutes.
Security reports show messaging apps, especially Telegram, account for a significant share of phishing incidents in crypto.
Fake Crypto Apps
Attackers distribute malware disguised as wallet apps, portfolio trackers, or fake versions of popular exchanges. Some appear on third-party app stores, while others temporarily bypass official store reviews.
These apps steal private keys, log keystrokes, or simulate wallet interfaces to trick users into approving unauthorized transfers. Victims often believe they are using legitimate software due to identical design.
Security firms have documented multiple cases where fake wallet apps silently transmitted private keys to attacker-controlled servers.

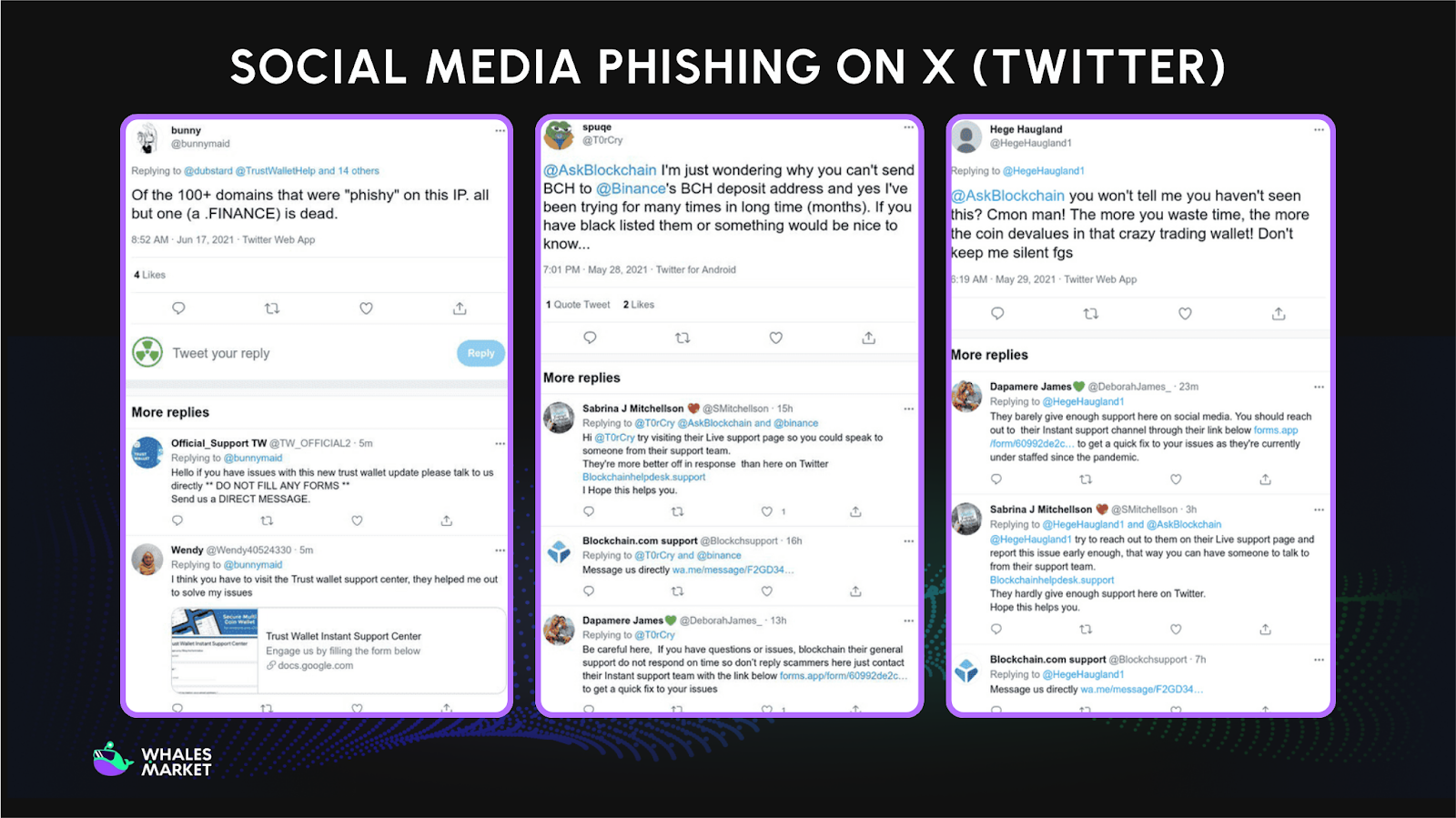
Social Media Phishing Attack on X
Scammers exploit X by impersonating exchanges, founders, or influencers to promote fake airdrops and giveaways. Posts often include phishing links, QR codes, or requests to connect wallets.
Fake verification badges, staged screenshots, and urgent calls to action are common tactics. Once a wallet is connected or a malicious contract is signed, attackers can drain funds or gain long-term token approvals.
Security researchers warn that social media giveaways remain a leading cause of wallet-drainer losses.
Notable Crypto Phishing Attack Examples
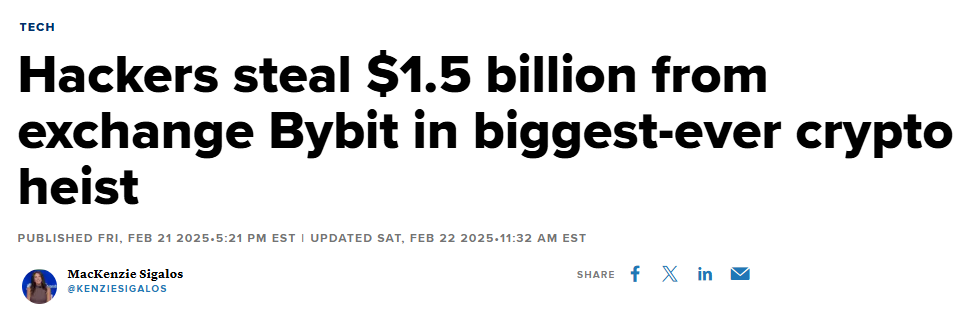
Bybit Hack (02/2025)
This incident is widely confirmed as the largest crypto hack in history. On February 21, 2025, approximately $1.5B worth of Ethereum was stolen from the Bybit exchange. The attackers are believed to be the Lazarus Group from North Korea, based on investigations by law enforcement and blockchain analytics firms.
Malware was used to interfere with internal systems, modifying a multisig transaction during the transfer from a cold wallet to a hot wallet. The transaction was silently redirected to attacker-controlled addresses. Most of the stolen assets were ETH, and the case highlighted how internal approval flows can be exploited through phishing-driven compromise.
$55.4M DAI Loss (08/2024)
Between August 20 and 22, 2024, a crypto whale lost around $55.4M in DAI stablecoins after signing a phishing transaction labeled “setOwner”. This single signature allowed attackers to gain control of a DSProxy and drain assets from a Maker Vault.
The attack made use of Inferno Drainer tooling and became one of the largest single-theft incidents of 2024. Security analysts later pointed to this case as a clear example of approval-based phishing, where no private keys or seed phrases were exposed, yet full asset control was lost.
Ledger Connect Kit Incident (12/2023)
On December 14, 2023, a former Ledger employee was phished, allowing attackers to gain access to NPMJS and publish a malicious version of the Ledger Connect Kit. Any users interacting with DApps that relied on this library during a roughly five-hour window were exposed to wallet-draining risks.
The malicious code deployed Angel Drainer and resulted in losses estimated between $484,000 and $600,000. Ledger removed the compromised package and compensated affected users. The incident was later analyzed in detail by multiple blockchain security firms and industry publications.
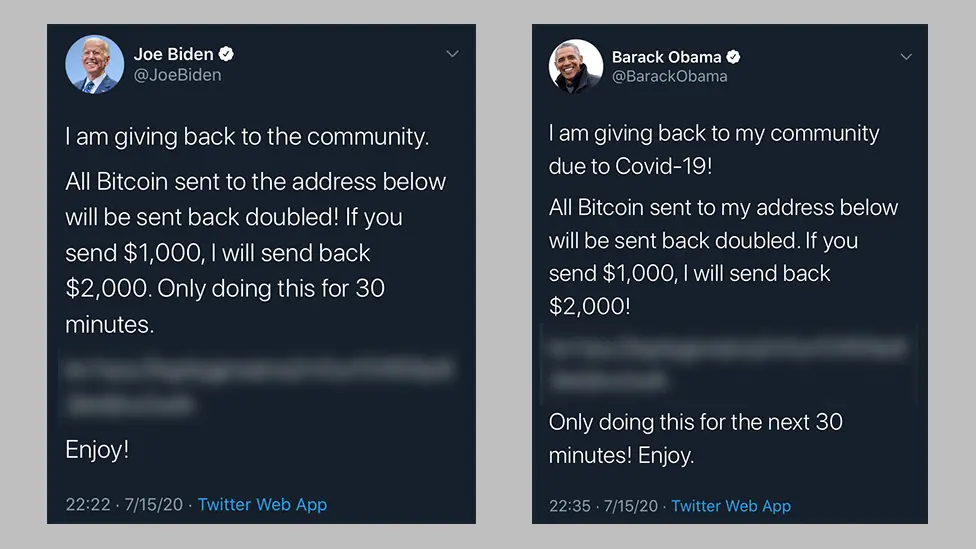
Twitter Bitcoin Scam (2020)
This incident occurred on July 15, 2020, when attackers used vishing techniques to trick Twitter employees into revealing internal login credentials. The attackers then hijacked accounts belonging to public figures such as Barack Obama, Elon Musk, Bill Gates, and Jeff Bezos.
Scam tweets promoted a classic scheme promising to double any Bitcoin sent. Within hours, hundreds of thousands to several million dollars were stolen. The perpetrators were later arrested, and the case was investigated by New York regulators and widely covered by major media outlets.
How to Prevent Phishing Attacks in Crypto
- Never Share or Enter Your Seed Phrase: Your seed phrase is the master key to your wallet. No legitimate wallet, exchange, or support team will ever request it. Never enter it into websites, forms, pop-ups, or messages. If your seed phrase is exposed, the wallet is permanently compromised.
- Verify URLs and Bookmark Official Websites: Always access exchanges, wallets, and DeFi platforms through saved bookmarks or official links. Phishing sites often differ by one character or use misleading extensions. Avoid clicking links from ads, replies, or DMs, even if the page looks identical to the real platform.
- Read Every Wallet Signature Carefully: Before signing any transaction, review what permissions you are granting. Be especially cautious with approvals, permits, and unlimited allowances. If a transaction requests permissions unrelated to your intended action, cancel immediately. A single careless signature can expose your entire wallet.
- Limit and Revoke Token Approvals Regularly: Only approve the exact amount of tokens needed for a transaction. Periodically review and revoke unused approvals using trusted tools. Old approvals remain active indefinitely and can be exploited later, even if you no longer use the original DApp that requested them.
- Separate Wallets by Risk Level: Use different wallets for different purposes. Keep long-term holdings in a cold or hardware wallet that never interacts with DApps. Use a hot wallet for daily transactions and a disposable “burner” wallet for new mints, airdrops, or experimental platforms.
- Ignore Unsolicited Messages and Offers: Phishing attacks rely on urgency and authority. Treat unsolicited DMs, emails, or messages claiming rewards, security issues, or exclusive access as suspicious by default. Legitimate projects do not contact users privately or pressure them to act immediately.
- Do Not Interact with Unknown Tokens or NFTs: Unexpected tokens or NFTs in your wallet may be bait. Interacting with them can trigger malicious smart contracts or approvals. The safest approach is to ignore, hide, or blacklist unsolicited assets rather than attempting to trade or investigate them.
- Use Security Tools and Transaction Simulations: Enable wallet features or browser extensions that simulate transactions and flag suspicious behavior. These tools help reveal hidden approvals, unusual contract calls, or known phishing sites before you sign. They act as an extra layer of defense, not a replacement for careful judgment.
Conclusion
Crypto phishing continues to evolve alongside the ecosystem itself. Awareness, patience, and consistent verification are now as important as technical knowledge. In crypto, long-term safety is built not by reacting fast, but by acting carefully every time.
FAQs
Q1: Which groups of users are most often targeted by crypto phishing scam?
Crypto phishing most often targets users who actively participate in DeFi, NFTs, airdrops, and newly launched DApps. Users who frequently sign on-chain transactions, grant wallet approvals, or experiment with unfamiliar platforms tend to face higher risk.
Q2: Why do many users not realize they have been phished immediately?
Many phishing attacks do not drain funds right away. Instead, attackers silently gain approval permissions and withdraw assets later, making it difficult for users to connect the loss to a transaction signed days or weeks earlier.
Q3: Does using a hardware wallet fully protect against crypto phishing attack?
Hardware wallets protect private keys from online theft, but they do not prevent phishing if a malicious transaction is approved. Once a valid signature is given, smart contracts can execute the granted permissions regardless of wallet type.
Q4: Can experienced crypto users still fall victim to phishing attack?
Experienced users can still be affected because modern phishing relies heavily on social engineering, familiar interfaces, and time pressure. Mistakes usually happen due to overconfidence or urgency, not a lack of technical understanding.
Q5: IS phishing a social engineering attack?
Social engineering exploits emotions such as fear, urgency, and FOMO to push users into acting quickly without proper verification. Because crypto transactions are irreversible, even one rushed or emotionally driven decision can lead to permanent and unrecoverable asset loss.
Q6: What crypto phishing attack prevention habit should users prioritize the most?
The most important habit is carefully reviewing every transaction before signing and only interacting with trusted websites, links, and tokens. Consistent caution significantly reduces the likelihood of falling victim to phishing attacks.