If users have ever read about Bitcoin mining or explored blockchain security, the term “nonce” likely appeared along the way. It may sound simple, but nonce plays a critical role in protecting cryptocurrency systems and modern security protocols. This article explains what a nonce is, how it works in blockchain, and why it matters in cryptography and network security.
What is a Nonce?
Nonce is commonly understood as a shortened form of “number used once.” It refers to a random or semi-random value created for a single use within a specific transaction or cryptographic operation.
The key idea behind a nonce is strict uniqueness. Each nonce is allowed to be used only one time in a given context. Once it has served its purpose, it must never be reused again in that same setting.
In blockchain systems, nonce serves two core conceptual roles:
- Block differentiation: enables miners to generate unique block hashes and reach consensus in Proof-of-Work.
- Transaction ordering: enforces a strict sequence of transactions per address, ensuring deterministic state changes.
- Security enforcement: prevents replay, duplication, and unauthorized reuse of blocks or transactions.
History and Origins of the Nonce
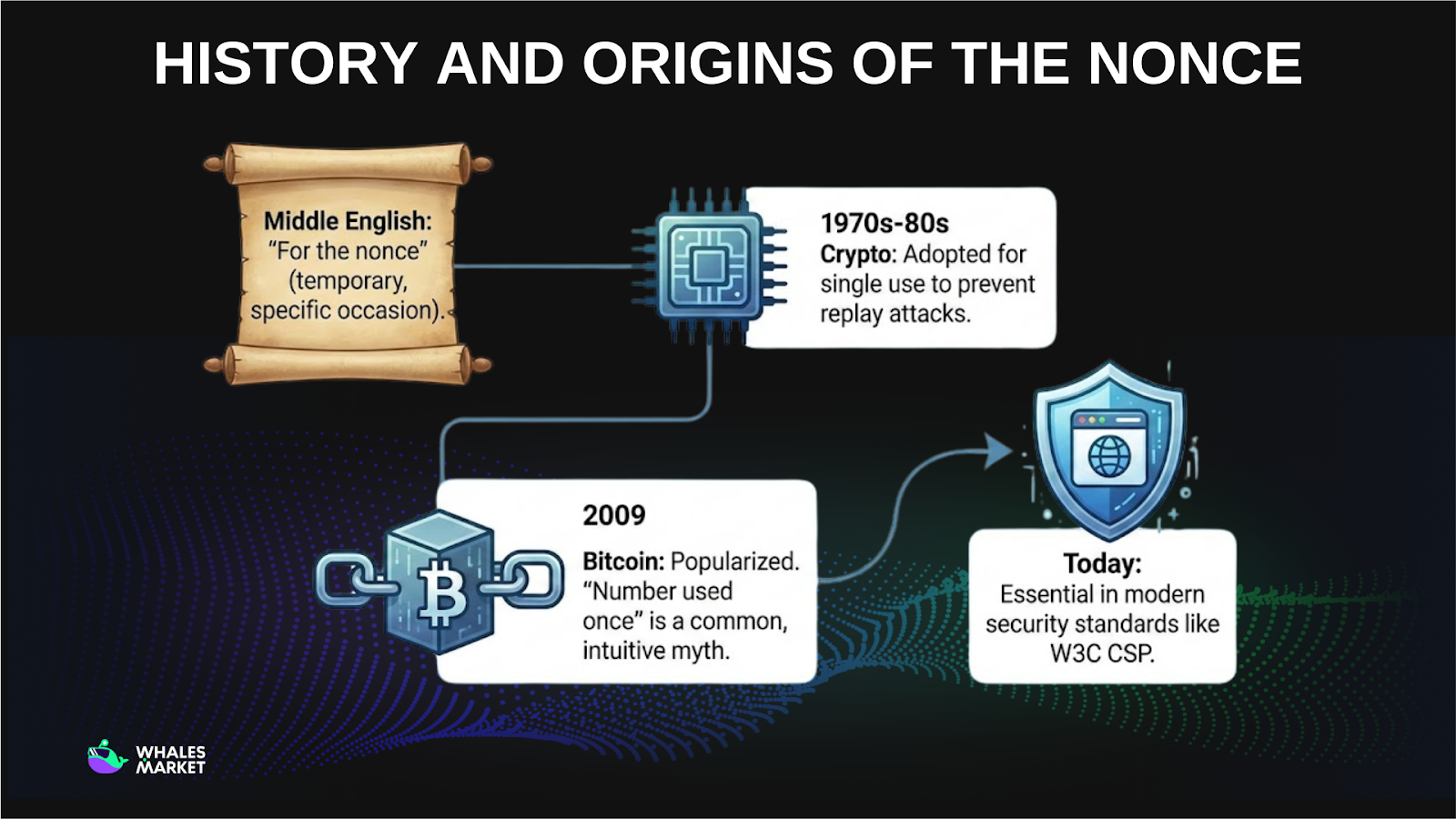
Nonce did not originate with digital technology. The word comes from Middle English, where it meant something used temporarily or for a specific occasion, derived from the phrase “for the nonce.” In modern cryptography, this meaning was adopted to describe values that exist only for a single use.
In technology, nonces began appearing in cryptographic systems during the 1970s and 1980s. Early security protocols such as Kerberos relied on nonces to prevent replay attacks, where an attacker reuses previously valid data to gain unauthorized access.
In 2009, with the launch of Bitcoin, nonce became widely known in the blockchain space. There is no formal proof that “number used once” is the official origin of the term. It is considered a folk etymology, but one that is intuitive and widely accepted.
Today, nonces remain a core part of modern security standards. They are used in areas such as web Content Security Policy (CSP), which has been standardized by the W3C since 2012 and continues to be updated through 2026 without major conceptual changes.
How does Nonce work in Blockchain?
In blockchain systems, nonce appears in two main contexts, each serving a different purpose.
Block Nonce
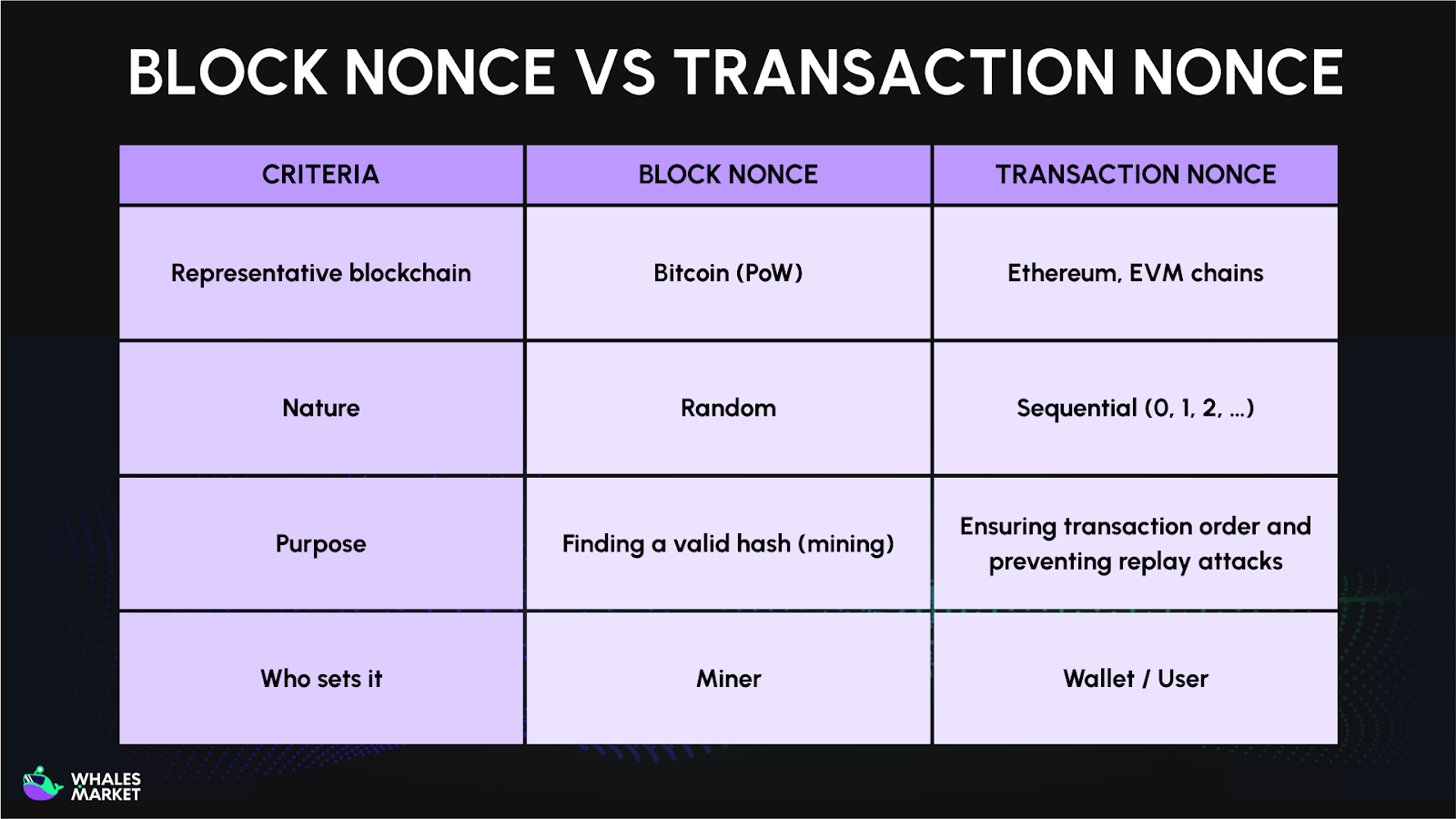
Block nonce is a fundamental component of the Proof-of-Work (PoW) consensus mechanism used by Bitcoin (BTC) and many other blockchains.
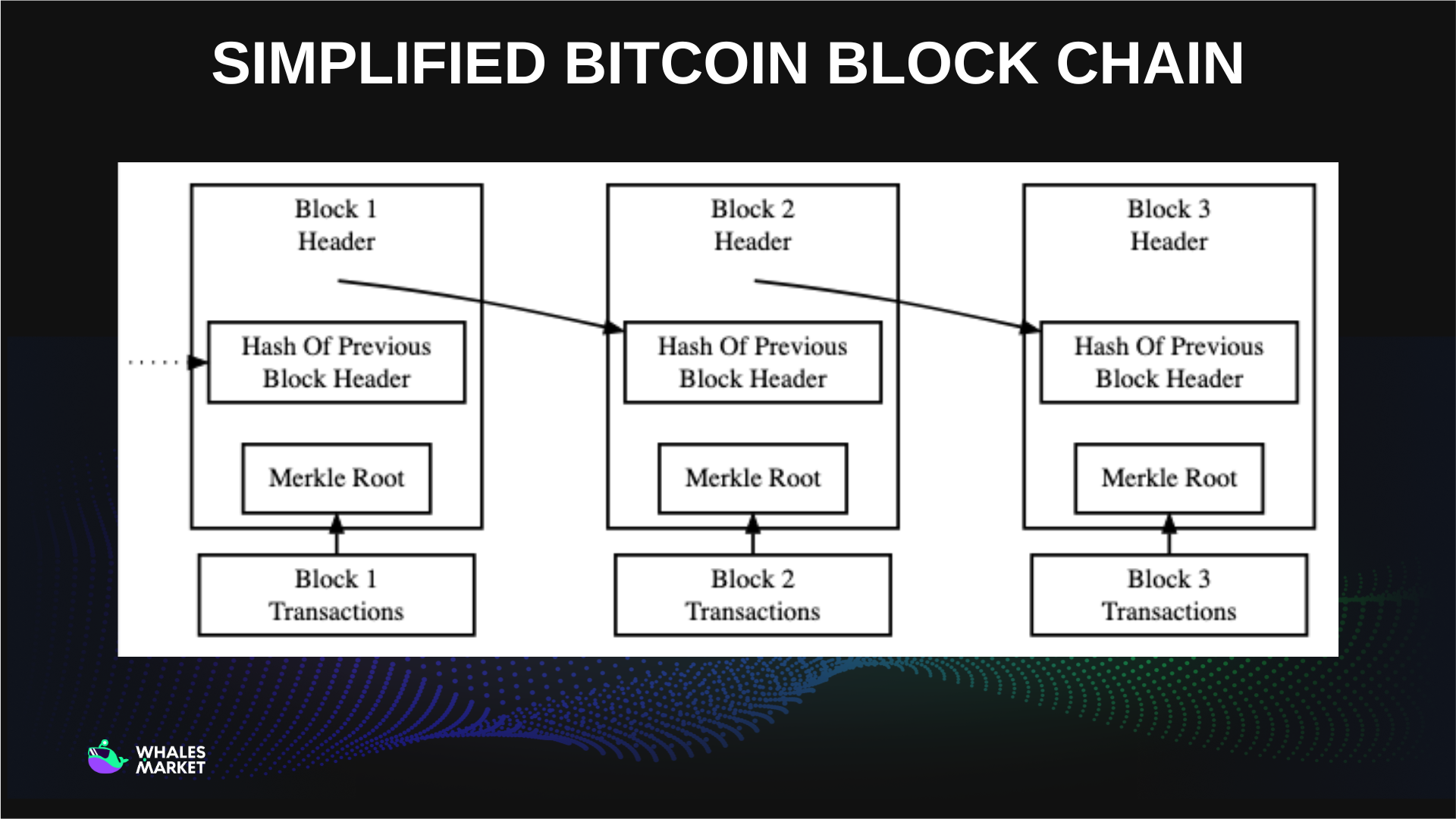
To understand how a block nonce works, it helps to first look at the basic structure of a blockchain. A blockchain is composed of a sequence of blocks, and each block consists of two main parts:
- Transaction data: the list of transactions included in the block
- Block header: metadata that uniquely identifies the block within the chain
The block header functions as a unique fingerprint for the block. It contains several key fields, including:
- The hash of the previous block
- A timestamp
- The Merkle root of all transactions in the block
- The nonce, which is the only field miners can freely modify
When miners attempt to create a new block, most of the block header information is already fixed. The transactions have been selected, the previous block hash is known, and the timestamp is set. At this stage, the nonce becomes the primary variable miners can change to influence the final hash of the block.
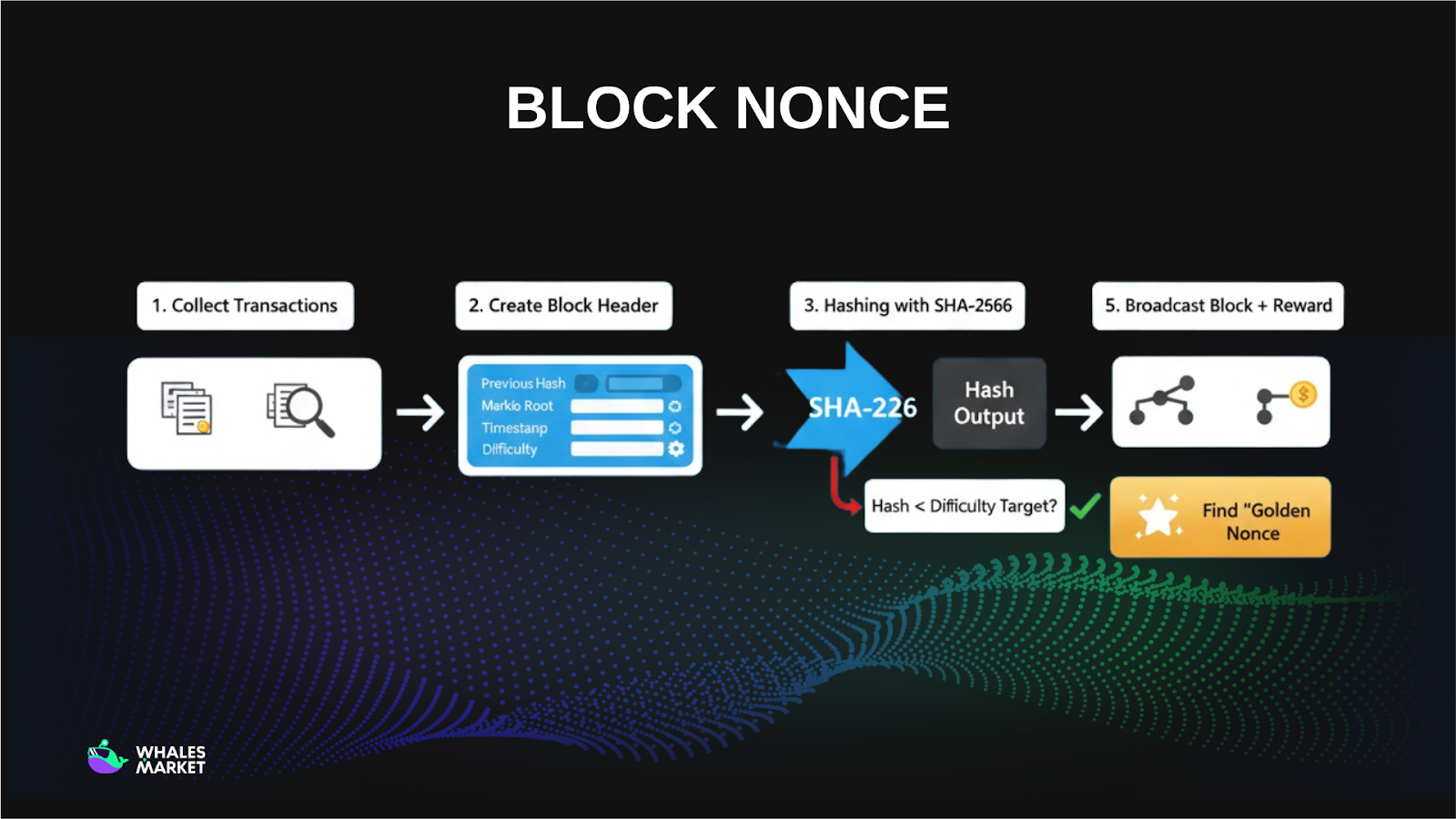
Mining itself is a trial-and-error process. Miners repeatedly:
- Change the nonce value
- Run the entire block header through a cryptographic hash function (such as SHA-256 in Bitcoin)
- Check whether the resulting hash satisfies the network’s difficulty requirement
Because cryptographic hash functions are unpredictable, each small change to the nonce produces a completely different hash output. If the hash does not meet the required difficulty threshold, the nonce is modified and the process repeats. This loop can run millions or even billions of times, as there is no shortcut other than performing large amounts of computation.
Once a miner discovers a nonce that produces a valid hash, the new block is broadcast to the network. Other nodes independently verify:
- The block hash
- The correctness of the included transactions
If the block is valid, it is added to the blockchain, and the miner receives a block reward along with transaction fees. In this way, the block nonce serves as proof that real computational work has been performed, forming the foundation of the Proof-of-Work consensus mechanism.
Transaction Nonce
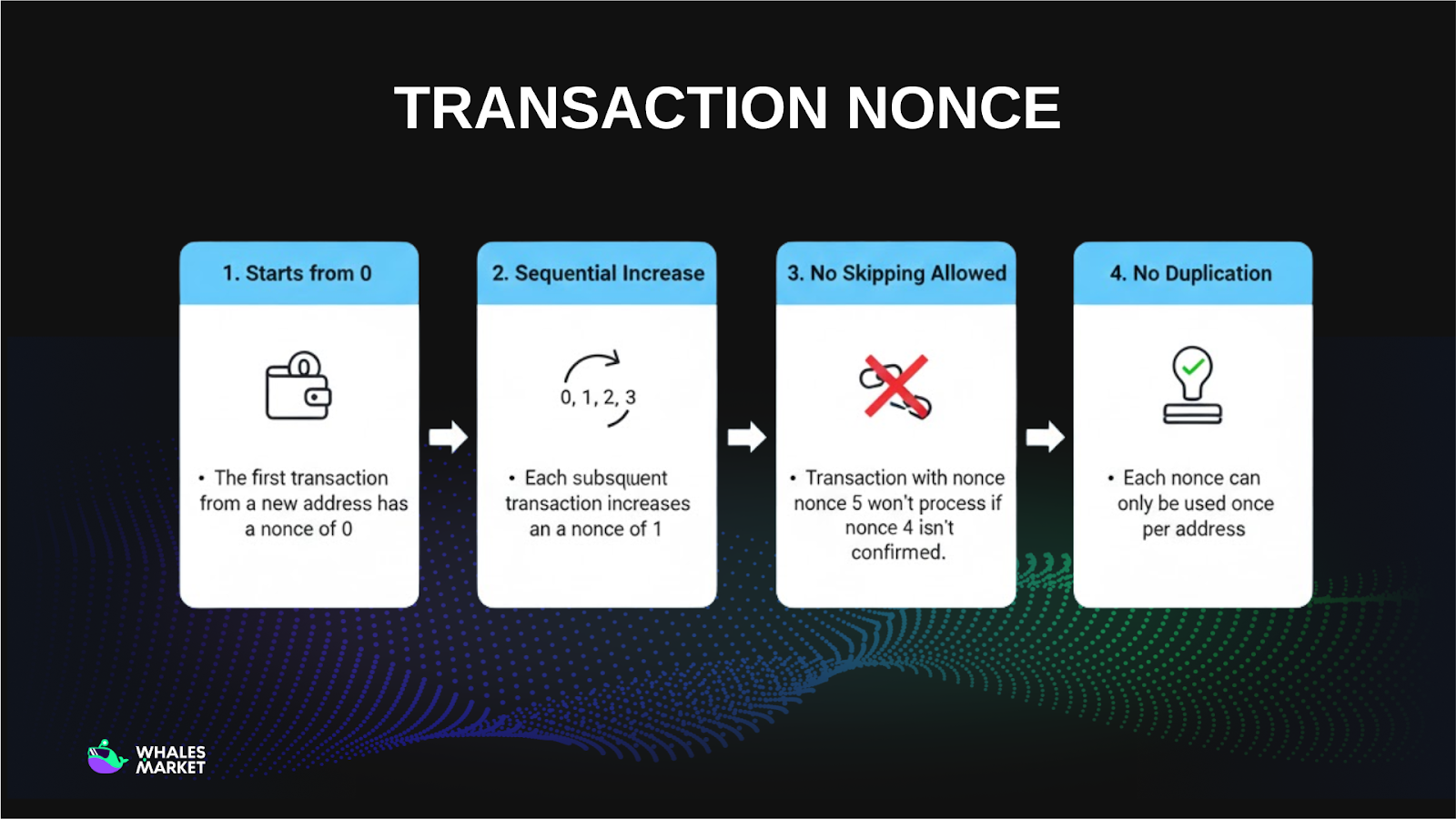
In Ethereum and other EVM-compatible blockchains, transaction nonce has a different meaning. It is a sequential counter that tracks how many transactions have been sent from a specific address.
A transaction nonce starts at zero for a newly created address. Each time the address sends a transaction, the nonce increases sequentially by one, forming a continuous sequence such as 0, 1, 2, 3, and so on. This sequential design allows the network to track how many transactions have been initiated from a specific account.
Because nonces must follow this strict order, transactions cannot be skipped or duplicated. If a transaction with nonce 5 is submitted before nonce 4 is confirmed, it will remain unprocessed until the missing nonce is resolved. Likewise, once a nonce has been used, it can never be reused by the same address, ensuring consistency and preventing replay.
Role of Transaction Nonce
- Ensures transaction order: In decentralized networks, nodes may receive transactions in different orders. The nonce guarantees that transactions are processed in the correct sequence.
- Prevents double spending: A transaction cannot be submitted twice because any reused nonce will be rejected by the network.
- Enables transaction replacement or cancellation: Users can submit a new transaction with the same nonce but a higher gas price to replace a pending transaction.
Block Nonce vs Transaction Nonce
Overall, nonce appears in blockchain in two distinct forms: block nonce and transaction nonce. While both serve the same fundamental purpose of ensuring uniqueness and preventing reuse, they operate at completely different layers of the system.
Block nonce focuses on block creation and consensus, whereas transaction nonce governs transaction ordering and state consistency.
Difficulty in Finding Block Nonce
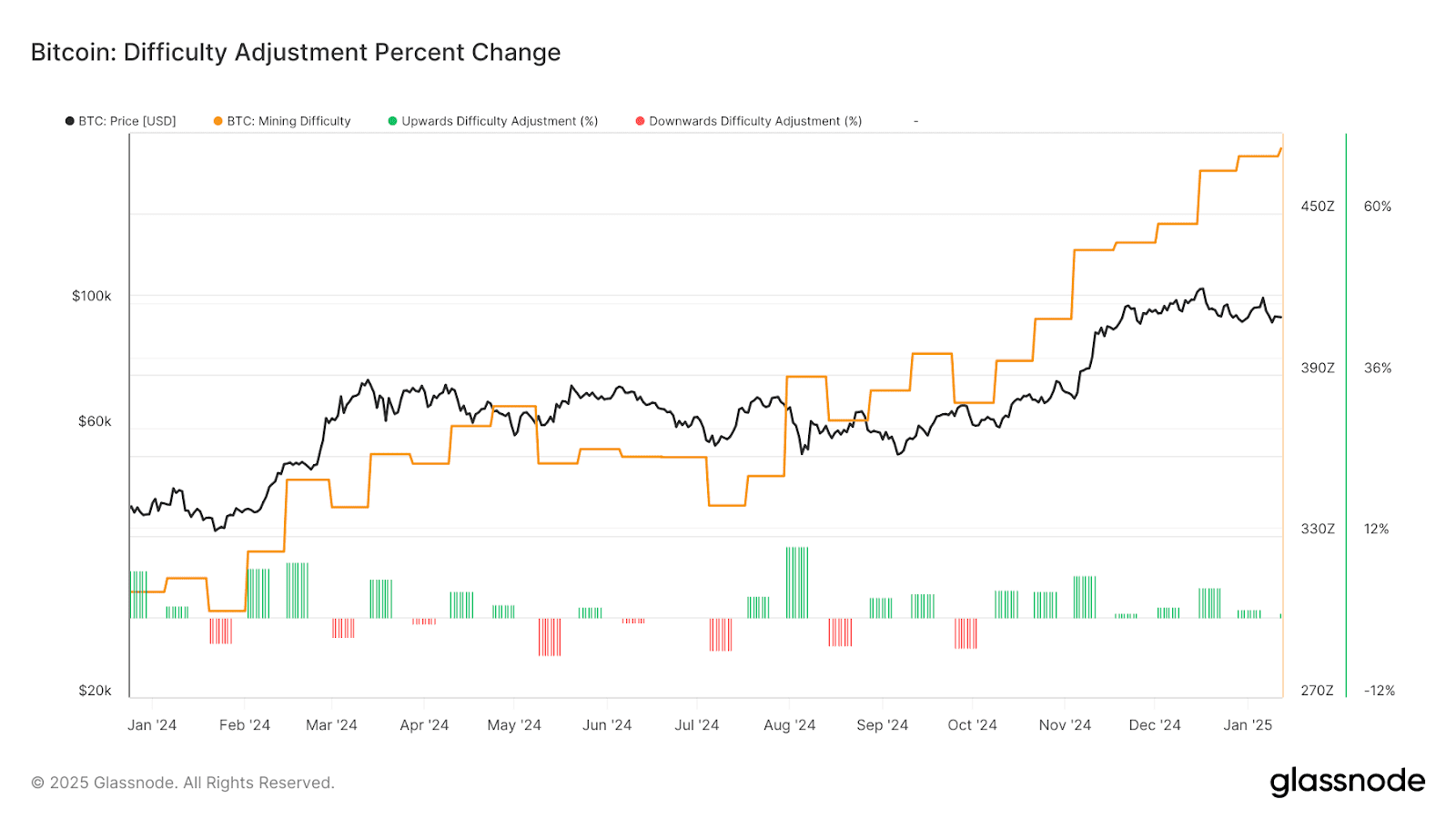
In Proof-of-Work blockchains such as Bitcoin, the difficulty of finding a valid block nonce is dynamically adjusted by the network. Bitcoin recalculates mining difficulty every 2,016 blocks (approximately every two weeks) to maintain an average block time of around 10 minutes, regardless of how much total computing power is participating.
As global hash power increases, the difficulty target is lowered, meaning that miners must search through a much larger space of possible nonces to produce a hash below the required threshold.
Historically, Bitcoin’s mining difficulty has grown by many orders of magnitude, rising from a value close to 1 in 2009 to tens of trillions in recent years. This reflects both rapid hardware advancement and intensified competition among miners worldwide.
Despite this continuous increase in difficulty, miners remain incentivized to participate because the system is designed around economic rewards. Successfully discovering a valid nonce grants the miner a block reward (newly issued coins) plus transaction fees included in the block.
Although individual miners face diminishing probabilities, the expected value of mining remains positive as long as rewards outweigh energy and infrastructure costs.
This self-adjusting mechanism creates a feedback loop between security and incentives: higher difficulty makes attacks more expensive, while rewards ensure that honest participation remains economically rational. As a result, increasing difficulty does not weaken the network but instead signals stronger competition and higher overall security.
Conclusion
Nonce may be small, but it is a quiet cornerstone of modern technology. From classical cryptography to blockchain systems and secure web standards, nonce protects data by enforcing uniqueness and preventing misuse.
Understanding nonce helps users grasp how blockchain truly works and provides essential knowledge for anyone involved in Web3, fintech, or cybersecurity.
FAQs
Q1. What does nonce mean?
A nonce is a value used only once to ensure uniqueness and prevent reuse or replay within a specific cryptographic or blockchain context.
Q2. How does nonce directly impact blockchain security?
Nonce ensures that each piece of data or transaction is processed only once within a defined context. This prevents reuse of old data, reduces the risk of replay attacks, and helps maintain the overall integrity and trustworthiness of blockchain networks.
Q3. What happens if a transaction nonce is incorrect?
When a transaction nonce is out of sequence, the network will reject the transaction or keep it pending. This often blocks subsequent transactions from the same address until the nonce issue is resolved or the transaction is replaced.
Q4. Does nonce affect transaction processing speed?
Nonce does not directly control transaction speed, but it influences transaction flow. An incorrect transaction nonce can delay all following transactions from an address, especially on EVM-compatible networks where strict ordering is enforced.
Q5. Why must block nonce be random in Proof-of-Work systems?
Randomness prevents miners from predicting valid hash outcomes in advance. This maintains fairness in mining, strengthens network security, and makes manipulation of block creation computationally impractical.
Q6. Do regular users need to understand nonce?
For most users, nonce is handled automatically by wallets. However, understanding nonce helps users troubleshoot stuck transactions, replace pending transactions correctly, and avoid common mistakes when interacting with blockchain networks.
Q7. Is nonce used outside of blockchain systems?
Yes. Nonce is widely used in web and network security, including session authentication, encryption protocols, and Content Security Policy implementations. In all cases, its purpose is to ensure uniqueness and prevent repeated or replayed attacks.

